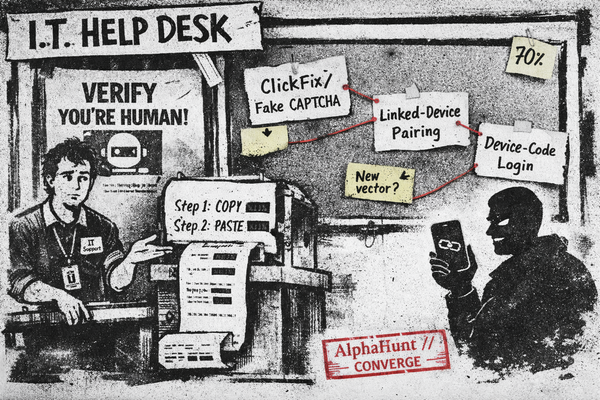
forecasts
ClickFix to Linked-Device Takeovers: Will Star Blizzard Introduce a New Initial-Access Vector by Oct 2026?
Fake CAPTCHA ➜ “paste this PowerShell.” 🙃 Linked-device pairing ➜ quiet account takeovers. 👻 Device-code phishing ➜ legit login page, attacker gets tokens. 🔑











