
PIR
Deepfake BEC & Payment Diversion: The Q1 2026 Fraud PIR You Can’t Defer
Deepfake BEC = the same old fraud… with a way better script. 🎭💸 If payroll/AP changes can happen on “sounds right,” you’re funding someone’s Q1 bonus.

PIR
Deepfake BEC = the same old fraud… with a way better script. 🎭💸 If payroll/AP changes can happen on “sounds right,” you’re funding someone’s Q1 bonus.

weekly
This week’s vibe: MongoBleed → KEV, BitLocker ransomware in critical infra, poisoned DNS “updates” for MgBot, and Aflac’s ~22.65M aftershock. 🔥🧨🦠

breaches
2025’s priciest breaches weren’t “elite malware.” They were tokens + SaaS + downtime 🪙⏱️🔥 If your revoke MTTR is measured in days, the attackers already won.

forecasts
Will hackers actually turn off a city’s water, or is that just conference-slide horror fiction? 💧🤔 We put a number on it...

weekly
🚨 CodeRED alerts ransomed. 🐛 Shai Hulud 2.0 looting CI/CD secrets. 📱 107 Android bugs + Albiriox on-device fraud. Signals Weekly on what to fix first.

forecasts
20% odds Akira triggers a 7-day ambulance diversion at a 10+ hospital system by end of 2026. 🚑 Still feeling “low risk”?

cl0p
LockBit got the Operation Cronos takedown. BlackCat imploded. Cl0p just logged a record leak month—and shows no sign of slowing. By 2026, do we really keep Cl0p dark for 90+ days… or just get Cl0p v2 with a fresh logo?
weekly
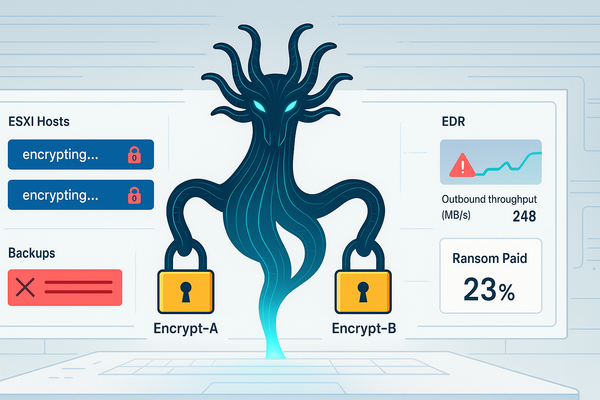
WSUS RCE is live—patch OOB now + watch 8530/8531. Payments fell to 23% in Q3 as crews pivot to insider bribes; Qilin doubles down on ESXi + EDR tamper.
cl0p
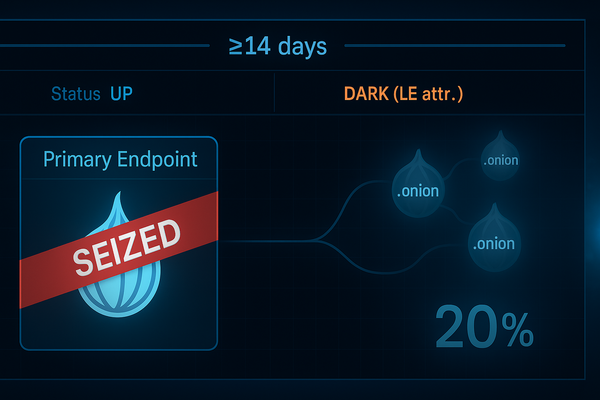
Forecast: 20% chance Cl0p’s leak sites go dark by Apr 22, 2026. Needs a seizure banner or ≥14 days down w/ LE attribution. Cronos showed it’s doable; mirrors make it brutal.

cl0p
Oracle EBS got in-memory Java loaders, not lockerware. Patch CVE-2025-61882, lock egress, hunt TemplatePreviewPG with TMP|DEF + XSL-TEXT|XML. Extortion rides in via “pubstorm.”
zero-day
This Week's Threat Intel Pulse: Oracle EBS zero-day exploited before patches dropped, Storm-1175 abuses GoAnywhere MFT, payroll hijackers hit US universities, ransomware crews weaponize Velociraptor, and a $15B Southeast Asian scam network faces global sanctions.

ransomware
Hybrid attacks are hitting navigation and port systems harder than ever — from ransomware to GPS spoofing — threatening safety, operations, and global trade.