
weekly
SIGNALS WEEKLY: Active Ivanti EPMM Zero-Days — What Defenders Must Do Now
Your control plane isn’t infrastructure. It’s leverage. 🔥

weekly
Your control plane isn’t infrastructure. It’s leverage. 🔥
forecasts
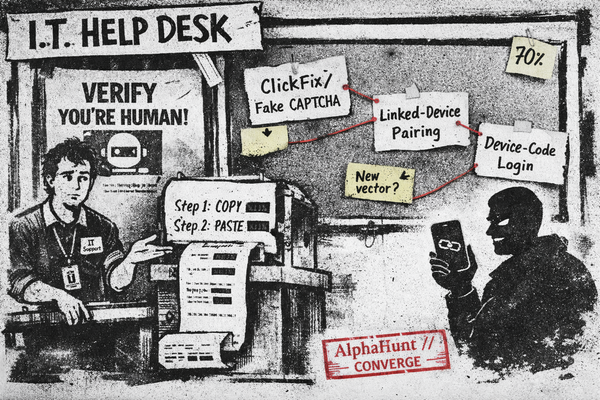
Fake CAPTCHA ➜ “paste this PowerShell.” 🙃 Linked-device pairing ➜ quiet account takeovers. 👻 Device-code phishing ➜ legit login page, attacker gets tokens. 🔑

weekly
🛫 Your “management plane” is now the battlefield. Cisco Secure Email + HPE OneView are seeing active exploitation, and UAT-8837 is chasing CI targets. Patch like it’s a fire drill. 🔥🧯

weekly
🎄 Zero-day season: Cisco AsyncOS exploited + KEV edge scramble. 🧯 VNC-to-HMI + cloud C2 (Drive/Telegram) keep paying rent.

russia
Russia-linked actors leaned hard on OAuth device codes and RDP phishing from Oct 2024–Aug 2025. Providers pushed back in concert. Here’s what changed, what to watch in your logs, and the quickest moves that buy real risk reduction.

lap-dogs
LapDogs, PolarEdge, and Volt Typhoon represent a new wave of China-linked ORB (Operational Relay Box) networks, each leveraging compromised SOHO routers, IoT devices, and enterprise infrastructure to conduct targeted, persistent espionage. LapDogs, first identified in 2025, uses the "ShortLeash"..

iran
Iranian cyber threat actors have evolved into highly capable, multi-motivated operators, leveraging both state sponsorship and ransomware affiliate partnerships to conduct espionage, sabotage, and financially motivated attacks. In 2025, the Iran-Israel conflict has catalyzed a surge in..

sandworm
Sandworm, a Russian GRU-affiliated cyber threat group (Unit 74455), continues to escalate its offensive cyber operations, with a primary focus on Ukraine and Western allies. The group is notorious for high-impact attacks such as the 2015-2016 Ukrainian power grid blackouts...

void-blizzard
Void Blizzard, a Russian state-sponsored APT attributed to the GRU and tracked as Laundry Bear by Dutch intelligence, has rapidly emerged as a major cyber espionage threat since April 2024. The group targets government, defense, telecommunications, NGOs, and critical infrastructure across NATO...

russia
LOSTKEYS, first observed in early 2025, marks a significant evolution in Russian cyber-espionage, attributed to the FSB-backed COLDRIVER group. Unlike traditional spear-phishing, LOSTKEYS employs a sophisticated multi-stage infection chain initiated by fake CAPTCHA lure websites (ClickFix)...

wizards
TheWizards is a China-aligned APT group, active since at least 2022, specializing in espionage and influence operations across Asia and the Middle East. Their hallmark is the use of IPv6 SLAAC spoofing to hijack legitimate software update mechanisms—most notably Tencent QQ..

purplehaze
PurpleHaze, an emerging Chinese state-sponsored threat group, operates highly dynamic multi-hop ORB networks that blend compromised IoT devices (notably SOHO routers with vulnerable firmware) and provisioned VPS to obscure command-and-control (C2) infrastructure.