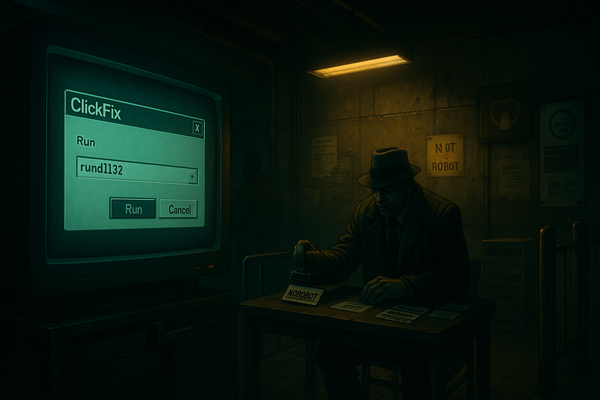
unc6485
Triofox Exploitation Cluster (UNC6485): Six-Month Outlook, Copycat Risk, and What to Watch
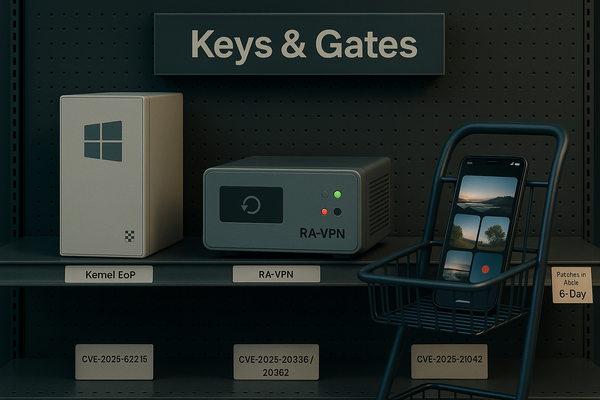
UNC6485 is farming Triofox: Host: localhost → setup → mint admin → AV path = your script → SYSTEM → RMM + reverse RDP/443. Patch to 16.7.10368.56560 now. Copycats next. 🔥🛡️