Triofox Exploitation Cluster (UNC6485): Six-Month Outlook, Copycat Risk, and What to Watch
UNC6485 is farming Triofox: Host: localhost → setup → mint admin → AV path = your script → SYSTEM → RMM + reverse RDP/443. Patch to 16.7.10368.56560 now. Copycats next. 🔥🛡️
TL;DR
- Access-broker standardization (60–75%): RMM footholds, reverse tunnels, scripted reseeding after eviction.
- Copycat proliferation (55–70%): Public exploit + AV-path execution abused across Triofox-like admin UIs.
- Identity pivot (40–55%): Local admin → domain groups, LSA/DPAPI harvest, scheduled rebuild of RMM.
- Tunnel obfuscation (25–35%): Shift to relay-style egress on 443; note 8443 only if supported by your own telemetry.
AlphaHunt
Stop doomscrolling, start decisioning. We chewed through the muck so your team doesn’t have to. → Subscribe! • Forward to your on-call lead.
(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
Ground Truth
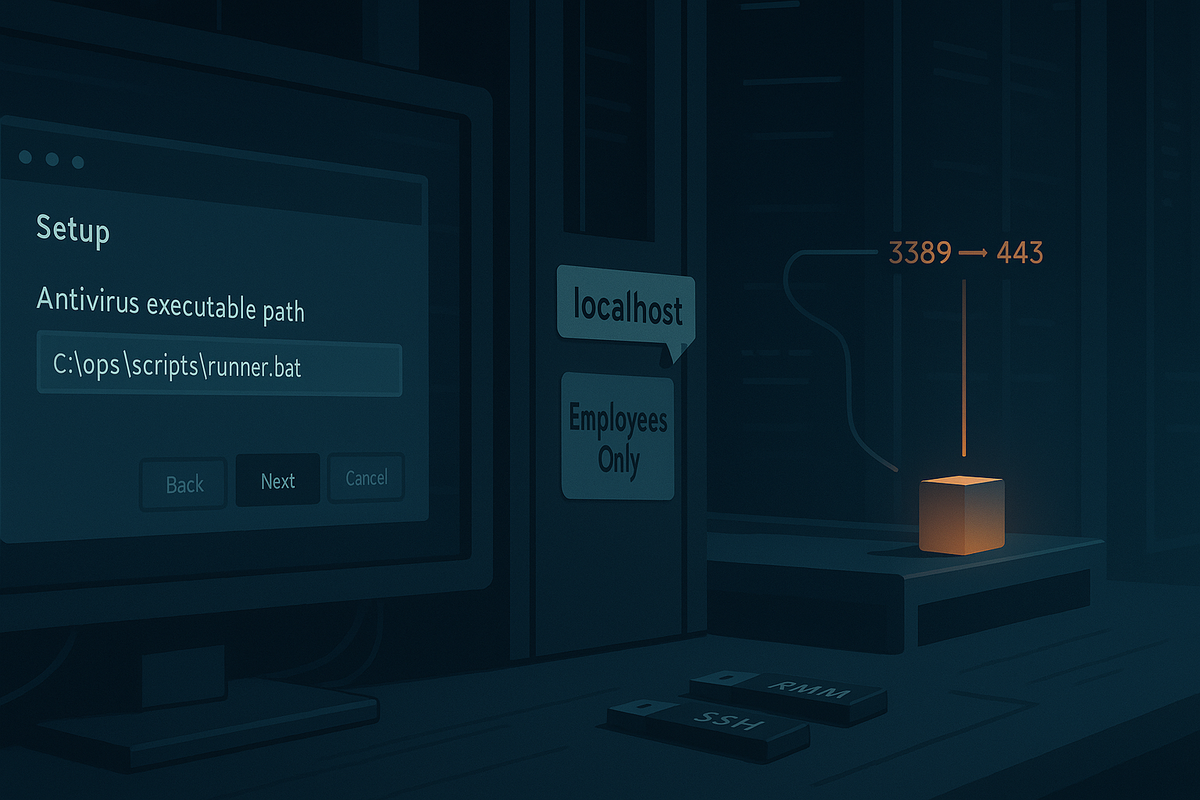
- Initial access: Host-header
localhostbypass to Triofox setup; actor creates native admin (CVE-2025-12480). - Privilege/exec: AV engine path re‑pointed to attacker script → SYSTEM execution via UI.
- Post-ex: Zoho UEMS/Assist, AnyDesk; RDP over SSH with plink/putty (often renamed:
sihosts.exe,silcon.exe), execution fromC:\Windows\appcompat\/C:\Windows\Temp\. - Infra: Low-cost VPS; reverse SSH forwarding of 3389 over 443; modest churn.
Attribution Outlook
- Actor of record: UNC6485 — 0.80
- Overlaps: exact initial access + AV-path abuse, RMM usage, renamed binaries, cheap VPS patterns.
- Comparators (look-alikes, lower confidence):
- UNC3944 / Scattered Spider — 0.10
- Overlap: hands-on-keyboard, RMM usage. Missing: SIM-swap/OAuth/helpdesk social-engineering play.
- FIN12 / UNC1878 — 0.07
- Overlap: pre-ransomware tradecraft echoes. Missing: exfil/locker staging.
- Access-broker archetypes — 0.03
- Overlap: commodity tunnels, resale-ready access. Weak: infra reuse evidence.
- UNC3944 / Scattered Spider — 0.10
Six‑Month Evolution
Access-broker standardization — 60–75%
- Leading indicators: instant RMM install post-setup, admin group adds, scripted reseed tasks after eviction.
- Falsifiers: vendor hardening disables setup path; AV-path writes blocked in UI/API.
Copycat proliferation — 55–70%
- Leading indicators: scanning of Triofox‑like products; pastebin/playbook reuse; GitHub PoCs for AV‑runner abuse.
- Falsifiers: rapid patch uptake; UI changes removing risky path controls.
- Note: CentreStack adjacency is speculative unless explicitly sourced—treat as hypothesis.
Identity/privilege pivot — 40–55%
- Leading indicators: local→domain group changes, password resets, LSA/DPAPI artifact creation; scheduled tasks/services to rebuild RMM.
- Falsifiers: EDR blocks credential materialization from Triofox/IIS lineage; AD monitoring flags are quiet.
Tunnel obfuscation — 25–35%
- Leading indicators: relay use (cloudflared/ngrok‑like), cert churn, 443‑only egress; JA3/ALPN shifts.
- Falsifiers: egress filtering + TLS/JA3 anomaly controls catching relays; SSRF/relay blocks at perimeter.
AV/execution‑hook generalization — 30–45%
- Leading indicators: abuse of other security‑tool “scan/repair/update” runners for SYSTEM execution via admin UIs.
- Falsifiers: vendors enforce signed‑path allowlists and isolate service accounts.
What Moves the Forecast
- Up‑shift to ransomware track (+15–25% FIN12‑like): discovery of exfil scaffolding, lockers staged, domain‑wide GPO edits.
- Tilt toward UNC3944 (+10–20%): SIM‑swap/helpdesk/OAuth abuse; cloud console pivots.
AlphaHunt Converge - Plug in your Flight Crew
Get intelligence where it counts. No dashboards. No detours. AlphaHunt Converge teases out your intent, reviews the results and delivers actionable intel right inside Slack. We turn noise into signal and analysts into force multipliers.
Anticipate, Don’t Chase.



![[DEEP RESEARCH] Who’s Most Likely to Abuse MCP Integrations? UNC3944, TraderTraitor, UNC6293](/content/images/size/w600/2026/03/z.png)

![[FORECAST UPDATED] AI Agents as Regulated C2: Will Anyone Be Forced to Act?](/content/images/size/w600/2026/02/z-11.png)
![[FORECAST] Fortune 500s: Will Prompt Injection Trick IDE Agent Mode into Running Commands—or Leaking Secrets—by 2026?](/content/images/size/w600/2026/02/z-10.png)