Signals Weekly: Active WSUS Exploits and Ransomware Shifts
WSUS RCE is live—patch OOB now + watch 8530/8531. Payments fell to 23% in Q3 as crews pivot to insider bribes; Qilin doubles down on ESXi + EDR tamper.
AlphaHunt Signals Weekly — Signal > Noise
I’m testing a new ~weekly product. It’s not another “link dump.” It’s a signal-ranked brief for operators who are busy and actually have to act.
TL;DR
- [Vulnerabilities] WSUS RCE (CVE-2025-59287) is actively exploited; added to KEV with an out-of-band Microsoft patch and concrete mitigations—prioritize patching and hunt for post-RCE AD lateral movement.
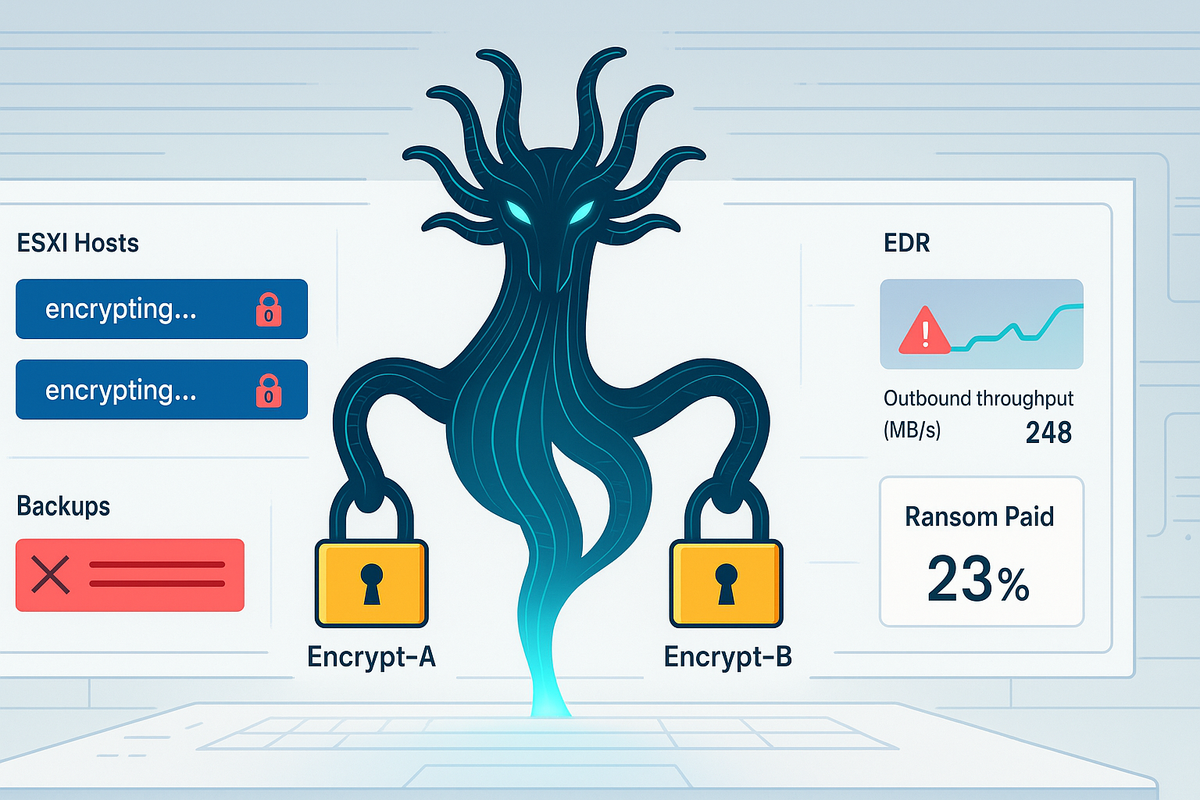
- [Ransomware] Qilin escalates impact across ESXi and backups with dual-encryptors, EDR tampering, and cloud exfil; meanwhile, ransom payment rates hit a record low as actors pivot to insider bribery and selective targeting.
- [Intrusion/Vulnerabilities] Emerging exposure: TP‑Link router RCEs and a SharePoint ToolShell surge enabling ransomware staging; Magento/Adobe Commerce KEV addition signals rising e‑commerce risk.
AlphaHunt
Stop doomscrolling, start decisioning. We chewed through the muck so your team doesn’t have to. → Subscribe! • Forward to your on-call lead.
(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
Current Stories
TL;DR
-
[Vulnerabilities] Active WSUS RCE at scale: CVE-2025-59287 added to KEV; OOB patch released; internet-exposed ports 8530/8531 are being hit now. New: Microsoft/CISA mitigation specifics + KEV addition.
-
[Threat Actors] Qilin ramps impact across virtualized estates: dual-encryptor ops, ESXi targeting, EDR tampering, cloud exfil via Cyberduck/Backblaze. New: detailed multi-case TTP flow incl. victim-specific creds embedded.
-
[Ransomware] Ecosystem under pressure: Q3 ransom payment rate drops to 23% (record low); actors pivot to insider bribery and selective “white whale” targeting. New: concrete payment metrics + documented insider-bribe case.
-
[Espionage] MuddyWater expands toolkit: Phoenix v4 backdoor via “FakeUpdate,” RMM abuse (Action1/PDQ), custom Chromium credential stealer, NordVPN for phish ops. New: Phoenix v4 + COM-based persistence artifacts and live C2 details.
-
[Policy/Defense] Water sector uplift: EPA publishes IR templates, incident action checklists, and a cybersecurity procurement checklist for utilities. New: first-party templates/utilities guidance now available.
References
-
(2025-10-24) CISA Adds Two Known Exploited Vulnerabilities to Catalog
-
(2025-10-27) CVE-2025-59287: Microsoft WSUS Remote Code Execution (Actively Exploited in the Wild)
-
(2025-10-26) Uncovering Qilin attack methods exposed through multiple cases
-
(2025-10-24) Insider Threats Loom while Ransom Payment Rates Plummet
-
(2025-10-23) EPA Releases New Resources to Help Protect Water Systems, Strengthen Cyber Resilience
-
(2025-10-22) MuddyWaters Espionage Campaign: Phoenix v4 Backdoor, FakeUpdate Injector, and Related Infrastructure
Suggested Pivots
WSUS exploitation: what process/identity chains are most predictive of post-RCE lateral movement in AD/Entra-heavy estates?
- Why: Prioritizes high-signal telemetry for early containment after CVE-2025-59287 exploitation.
- What to expect: Hunt queries, parent-child process trees, and identity abuse patterns to harden detections.
Qilin’s pre-encryption staging: which ESXi and backup-manipulation behaviors emerge earliest and most consistently?
- Why: Enables earlier detection in virtualized environments before impact escalates.
- What to expect: A shortlist of ESXi commands, PowerShell patterns, and RMM artifacts for proactive alerting.
AlphaHunt Converge - Plug in your Flight Crew
Get intelligence where it counts. No dashboards. No detours. AlphaHunt Converge teases out your intent, reviews the results and delivers actionable intel right inside Slack. We turn noise into signal and analysts into force multipliers.
Anticipate, Don’t Chase.
Emerging Stories
TL;DR
-
[Vulnerabilities] TP-Link Omada/Festa routers: new CVEs (2025-7850/7851) enable RCE/root via WireGuard UI injection and residual debug paths; some remote, unauthenticated scenarios. New: disclosure signals systemic LuCI weaknesses; more fixes due 2026.
-
[Intrusion Sets] ToolShell surge on SharePoint: unauth RCE chains (CVE-2025-53770/53771) drive lateral movement and follow-on ransomware; DFIR tool (Velociraptor) abused for persistence. New: quarter-over-quarter rise with concrete ops patterns.
-
[E‑crime] Magento/Adobe Commerce risk rising: CISA adds CVE-2025-54236 to KEV, indicating active exploitation potential against ecommerce stacks. New: KEV inclusion elevates patch urgency.
References
-
(2025-10-23) IR Trends Q3 2025: ToolShell attacks dominate, highlighting criticality of segmentation and rapid response
-
(2025-10-23) New TP-Link Router Vulnerabilities: A Primer on Rooting Routers
-
(2025-10-24) CISA Adds Two Known Exploited Vulnerabilities to Catalog
Suggested Pivots
TP-Link exposure: where do Omada/Festa management planes sit in our attack surface, and what compensating controls block CVE-2025-7850 paths?
- Why: Validates real-world exposure while patches roll out.
- What to expect: Asset inventory, ACL/WAF recommendations, and monitoring indicators by model/firmware.
ToolShell follow-on: how do SharePoint-to-database trust paths enable credential theft and ransomware staging?
- Why: Maps lateral movement edges unique to SharePoint estates.
- What to expect: Architecture weak points, hardening steps, and telemetry cues to break the chain early.
Appendix
References
-
(2025-10-24) CISA Adds Two Known Exploited Vulnerabilities to Catalog
-
(2025-10-27) CVE-2025-59287: Microsoft WSUS Remote Code Execution (Actively Exploited in the Wild)
-
(2025-10-26) Uncovering Qilin attack methods exposed through multiple cases
-
(2025-10-24) Insider Threats Loom while Ransom Payment Rates Plummet
-
(2025-10-23) EPA Releases New Resources to Help Protect Water Systems, Strengthen Cyber Resilience
-
(2025-10-22) MuddyWaters Espionage Campaign: Phoenix v4 Backdoor, FakeUpdate Injector, and Related Infrastructure
-
(2025-10-23) IR Trends Q3 2025: ToolShell attacks dominate, highlighting criticality of segmentation and rapid response
-
(2025-10-23) New TP-Link Router Vulnerabilities: A Primer on Rooting Routers
-
(2025-10-24) CISA Adds Two Known Exploited Vulnerabilities to Catalog
AlphaHunt
Stop doomscrolling, start decisioning. We chewed through the muck so your team doesn’t have to. → Subscribe! • Forward to your on-call lead.
(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
(c) 2025 CSIRT Gadgets, LLC




![[FORECAST] Dismantled or Displaced? Cambodia’s Scam-Compound Crackdown by 2030?](/content/images/size/w600/2026/02/z-7.png)

