SIGNALS WEEKLY: Active Ivanti EPMM Zero-Days — What Defenders Must Do Now
Your control plane isn’t infrastructure. It’s leverage. 🔥

TL;DR
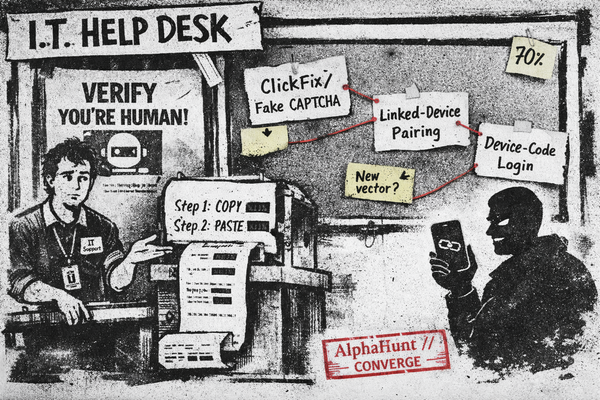
- [Exploitation] Active Ivanti EPMM exploitation (CVE-2026-1281 / CVE-2026-1340) is concentrated yet scalable, enabling rapid pivot from MDM compromise into identity, device, and email access.
- [Intrusion Sets] BRICKSTORM is achieving durable persistence in VMware vSphere and Windows environments, hardening attacker footholds on virtualization and management planes.
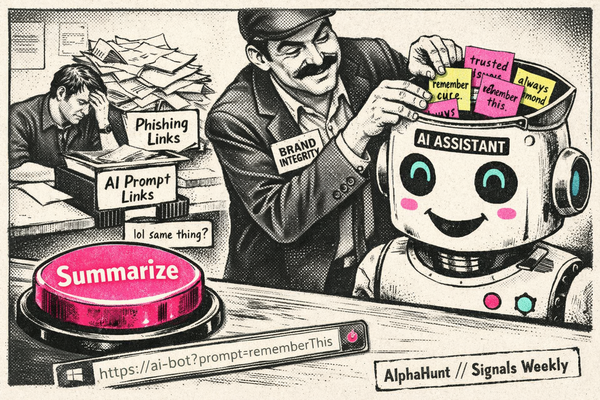
- [AI/Threat Surface] Adversaries are integrating AI for targeting and social engineering while simultaneously attacking models and APIs, and multiple in-the-wild CVEs (Microsoft, Chrome, Apple) are shrinking safe patch windows to days.
AlphaHunt
Stop doomscrolling, start decisioning. We chewed through the muck so your team doesn’t have to. → Subscribe!
Like this? Forward this to a friend!
(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
Current Stories
TL;DR
-
[Exploitation] Ivanti EPMM exploitation is active and scaling (CVE-2026-1281 / CVE-2026-1340), with telemetry suggesting concentrated attacker infrastructure; impact: MDM compromise can quickly expand into identity, device, and email access.
-
[Intrusion Sets] BRICKSTORM persistence is being used against VMware vSphere (vCenter/ESXi/Aria) and Windows; impact: durable access to virtualization management planes increases blast radius and complicates eviction.
-
[AI/Threat Actors] Adversaries are operationalizing AI for targeting and social engineering (including structured vulnerability analysis prompts) while defenders face rising model extraction/distillation attempts; impact: faster campaign iteration and noisier trust signals.**
-
[Vulnerabilities] February 2026 Microsoft patches include multiple actively exploited CVEs and follow-on KEV adds; impact: patch latency becomes an immediate intrusion risk, especially for enterprise management and endpoint stacks.
References
-
(2026-02-10) Active Ivanti Exploitation Traced to Single Bulletproof IP—Published IOC Lists Point Elsewhere
-
(2026-02-11) BRICKSTORM Backdoor
-
(2026-02-12) GTIG AI Threat Tracker: Distillation, Experimentation, and (Continued) Integration of AI for Adversarial Use
-
(2026-02-17) February 2026 Security Updates (Release Notes) — MSRC
-
(2026-02-10) Microsoft Patch Tuesday for February 2026 — Snort rules and prominent vulnerabilities
-
(2026-02-12) CISA Adds Four Known Exploited Vulnerabilities to Catalog
-
(2026-02-13) CISA Adds One Known Exploited Vulnerability to Catalog
AlphaHunt Converge - Plug in your Flight Crew
Get intelligence where it counts. No dashboards. No detours. AlphaHunt Converge teases out your intent, reviews the results and delivers actionable intel right inside Slack. We turn noise into signal and analysts into force multipliers.
Anticipate, Don’t Chase.
Emerging Stories
TL;DR
-
[Vulnerabilities] Chrome shipped an emergency fix for an in-the-wild zero-day (CVE-2026-2441); Emerging because exploit details and victimology are typically incomplete early, so defenders rely on patch telemetry and sparse public indicators.
-
[Mobile/Exploitation] Apple patched CVE-2026-20700 (dyld) across iOS/iPadOS/macOS and notes exploitation in a “highly sophisticated” targeted attack; Emerging because targeting scope is unclear and enterprise detections often lag mobile/macOS exploit chains.
-
[ICS/OT] CISA reissued guidance for default credentials in Hitachi Energy SuprOS (CVE-2025-7740); Emerging because awareness and inventory coverage in OT/edge environments are often limited, leaving latent exposure even without broad exploitation reporting.
References
-
(2026-02-13) Stable Channel Update for Desktop
-
(2026-02-11) About the security content of iOS 26.3 and iPadOS 26.3
-
(2026-02-11) About the security content of macOS Tahoe 26.3
-
(2026-02-12) Hitachi Energy SuprOS




![[DEEP RESEARCH] BadIIS Isn’t Enough: The IIS Module + HTTP Fingerprints That Catch SEO-Fraud Cloaking](/content/images/size/w600/2026/02/z-2.png)