Predatory Sparrow: Pro-Israel Hacktivist Group’s Destructive Cyber Operations Against Iranian Critical Infrastructure
Predatory Sparrow (Gonjeshke Darande) is a pro-Israel hacktivist group, likely state-affiliated, that has escalated destructive cyber operations against Iranian critical infrastructure since the early 2020s. Their attacks—most recently the June 2025 disruption of Bank Sepah—employ ransomware...

where do i get my ideas??? random social media posts...
(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
Get questions like this:
- what do you know about predatory sparrow?
- What specific malware families and tools has Predatory Sparrow used in their attacks?
Does it take a chunks out of your day? Would you like help with the research?
This baseline report was thoughtfully researched and took 10 minutes.. It's meant to be a rough draft for you to enhance with the unique insights that make you an invaluable analyst.
We just did the initial grunt work..
Are you ready to level up your skillset? Get Started Here!
Did this help you? Forward it to a friend!
Suggested Pivot
What specific initial access vectors—such as phishing campaigns, exploitation of known vulnerabilities in Iranian critical infrastructure systems, or supply chain compromises—has Predatory Sparrow likely employed, and how can these be detected or mitigated given the absence of publicly disclosed IOCs?
This question addresses a critical gap in understanding the group’s entry methods, enabling targeted defensive measures and improving early detection capabilities.
TL;DR
Key Points
-
- Predatory Sparrow, a pro-Israel hacktivist group with likely state affiliations, has executed highly disruptive cyberattacks against Iranian critical infrastructure, notably Bank Sepah, using destructive malware and denial-of-service (DoS) tactics.
- Defenders should prioritize advanced EDR with behavioral analytics, network segmentation, and DoS mitigation to counter these sophisticated, multi-vector attacks.
-
- The group’s operations focus on disruption and destruction (not data theft), leveraging ransomware/wiper-like payloads and coordinated DoS, with no public IOCs or malware signatures disclosed.
- Detection and response must rely on behavioral indicators, anomaly detection, and intelligence sharing due to the absence of technical indicators.
-
- Attribution remains circumstantial; Predatory Sparrow is widely believed to be linked to Israeli military intelligence, but no definitive public evidence exists.
- Organizations should monitor for evolving TTPs and anticipate further escalation amid ongoing Israel-Iran tensions.
-
- The group employs psychological operations and public messaging to amplify the impact of attacks, aiming to erode Iranian public morale and influence international perceptions.
- Security teams should integrate cyber threat intelligence (CTI) and counter-influence strategies into their defensive posture.
Executive Summary
Predatory Sparrow (Gonjeshke Darande) is a pro-Israel hacktivist group, likely state-affiliated, that has escalated destructive cyber operations against Iranian critical infrastructure since the early 2020s. Their attacks—most recently the June 2025 disruption of Bank Sepah—employ ransomware/wiper-like malware (MITRE T1486) and coordinated DoS (T1499) to cause operational outages in banking, energy, and industrial sectors. The group’s TTPs include exploitation of network vulnerabilities, possible social engineering, and use of web protocols for command and control (T1071.001), but no specific malware or IOCs have been publicly disclosed, complicating technical attribution and detection.
Predatory Sparrow’s operations are characterized by a focus on disruption and destruction rather than data exfiltration, aligning with strategic objectives to weaken Iranian state capabilities and exert geopolitical pressure. Their public messaging and psychological operations amplify the impact of attacks, contributing to regional instability and shaping adversary perceptions.
Defensive recommendations include deploying advanced EDR with behavioral analytics, enforcing network segmentation and zero trust, implementing robust DoS mitigation, enhancing CTI integration, and conducting targeted social engineering training. Given the group’s operational security and evolving tactics, defenders must rely on behavioral detection, intelligence sharing, and continuous adaptation of security controls.
Forecasts indicate continued escalation of destructive attacks, increased operational security by the group, and further integration of cyber and psychological operations within the broader Israel-Iran conflict. Long-term, the institutionalization of cyber conflict and the evolution of destructive malware—potentially with AI-driven automation—are likely, necessitating ongoing investment in critical infrastructure defense and regional intelligence collaboration.
Research & Attribution
Historical Context
Predatory Sparrow, also known by its Persian name Gonjeshke Darande, is a pro-Israel hacktivist group that gained prominence in the early 2020s for targeting Iranian critical infrastructure. The group has claimed responsibility for cyberattacks disrupting Iranian fuel stations, banking systems, and state-owned industrial facilities. Their activities are part of the broader cyber conflict between Israel and Iran, reflecting escalating digital hostilities that mirror geopolitical tensions in the region. While presenting as hacktivists, Predatory Sparrow is widely believed by cybersecurity experts and intelligence analysts to have links to Israeli military intelligence or state-affiliated actors, though definitive public attribution remains unconfirmed.
Timeline
- Early 2020s: Emergence of Predatory Sparrow with initial attacks on Iranian infrastructure.
- June 2022: Attack on three Iranian state-owned foundries, reportedly causing a fire.
- 2024-2025: Increased cyber operations targeting Iranian fuel stations, rail systems, and banks.
- June 2025: Public claims of a major cyberattack disrupting Bank Sepah, Iran's largest bank, causing outages in banking services and fuel payment systems amid escalating Israel-Iran conflict.
Origin
Predatory Sparrow is attributed to a pro-Israel hacktivist collective, likely linked to Israeli military intelligence or state-sponsored cyber operations. The group uses the Persian name Gonjeshke Darande, indicating a focus on Iranian targets and cultural context. Although Israel does not officially acknowledge offensive cyber operations, multiple high-impact cyber incidents against Iran have been attributed to Israeli state-linked groups, with Predatory Sparrow fitting this pattern. The group’s operational security and selective impact suggest possible legal or strategic constraints governing their activities.
Countries Targeted
- Iran – The primary and almost exclusive target, focusing on critical infrastructure such as banking, energy, and industrial sectors.
Sectors Targeted
- Financial Sector – Attacks on Bank Sepah and other financial institutions to disrupt economic operations and sanctions circumvention.
- Energy Sector – Disruption of fuel stations and related infrastructure to impact energy supply and logistics.
- Industrial Sector – Targeting state-owned foundries and manufacturing facilities linked to Iran’s military and nuclear programs.
Motivation
Predatory Sparrow is motivated by political and ideological objectives aligned with pro-Israel interests. Their operations aim to disrupt Iranian state infrastructure, weaken economic and energy capabilities, and exert pressure on Tehran amid ongoing regional conflicts. The group uses hacktivism as a cover, blending political activism with cyber warfare tactics to achieve strategic impact.
Attack Types
Predatory Sparrow employs a range of destructive and disruptive cyberattack techniques, including:
- Data destruction and encryption (MITRE ATT&CK T1486) to cause operational outages and damage.
- Denial of service attacks (T1499) targeting critical infrastructure endpoints such as fuel stations.
- Use of web protocols for command and control communications (T1071.001).
- Coordinated multi-vector attacks combining disruption of banking services, fuel payment systems, and industrial operations.
- Psychological operations through public claims and messaging to influence perception and morale.
Technical Details and TTPs
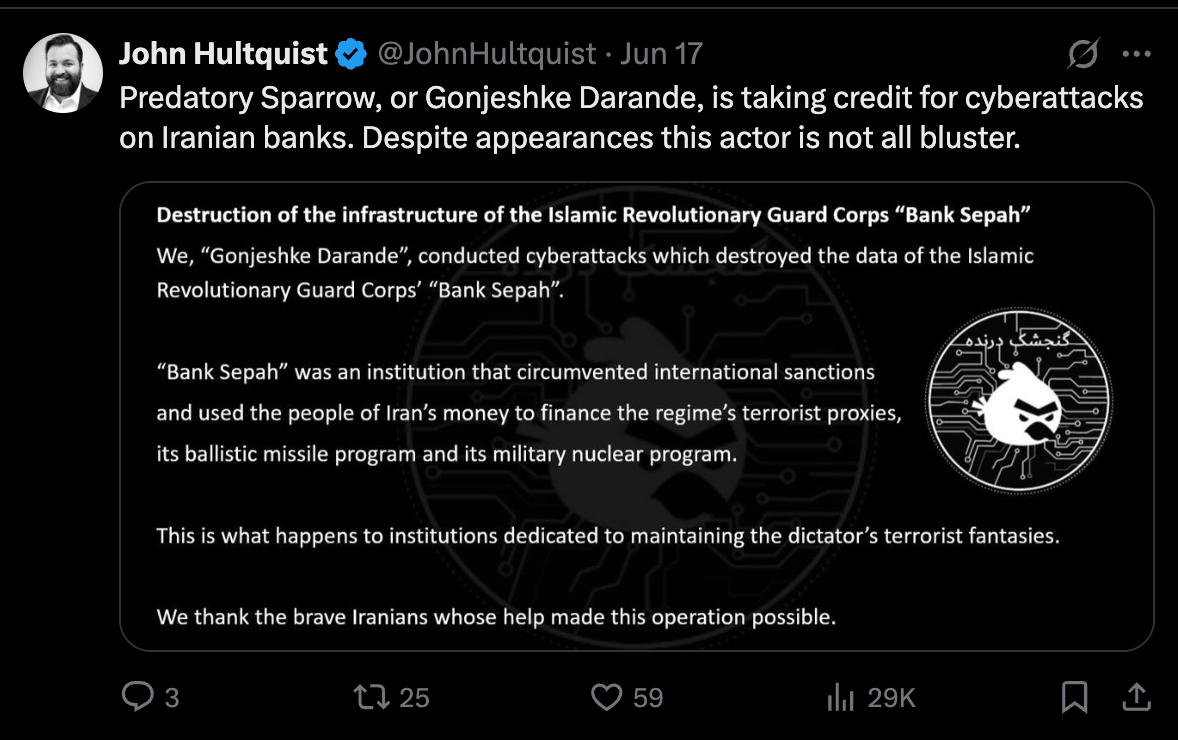
- The group has claimed responsibility for attacks that destroyed data belonging to the Islamic Revolutionary Guard Corps' Bank Sepah, causing widespread service outages.
- Attack vectors include exploitation of network vulnerabilities and possibly social engineering to gain initial access, though specific initial access methods remain unconfirmed publicly.
- No specific malware families or custom tools have been definitively attributed to Predatory Sparrow in open-source intelligence or MITRE ATT&CK databases.
- The group’s destructive payloads resemble ransomware or wiper malware, designed to encrypt or erase data to disrupt operations rather than for financial gain.
- Indicators of compromise (IOCs) such as file hashes or command and control infrastructure have not been publicly disclosed.
- Operational tactics include reconnaissance (TA0007), command and control (TA0011), and impact (TA0040) phases, consistent with sophisticated cyber operations targeting critical infrastructure.
Known Aliases
- Predatory Sparrow (Google Threat Intelligence Group)
- Gonjeshke Darande (Persian name used by the group and recognized by analysts)
Key Takeaways
- Predatory Sparrow is a pro-Israel hacktivist group targeting Iranian critical infrastructure, especially banking and energy sectors.
- The group uses destructive cyberattacks to disrupt services, including data destruction and denial of service.
- While publicly presenting as hacktivists, they are widely believed to have state affiliations, likely linked to Israeli military intelligence.
- Their attacks have caused significant operational outages, including a major disruption of Bank Sepah in June 2025.
- No specific malware or IOCs have been publicly disclosed, but their tactics align with sophisticated cyber warfare operations.
- Attribution remains circumstantial, with no definitive public evidence linking them to a specific government entity.
Recommendations, Actions, Suggested Pivots, Forecasts and Next Steps
(Subscribers Only)



![[FORECAST UPDATED] AI Agents as Regulated C2: Will Anyone Be Forced to Act?](/content/images/size/w600/2026/02/z-11.png)
![[FORECAST] Fortune 500s: Will Prompt Injection Trick IDE Agent Mode into Running Commands—or Leaking Secrets—by 2026?](/content/images/size/w600/2026/02/z-10.png)
