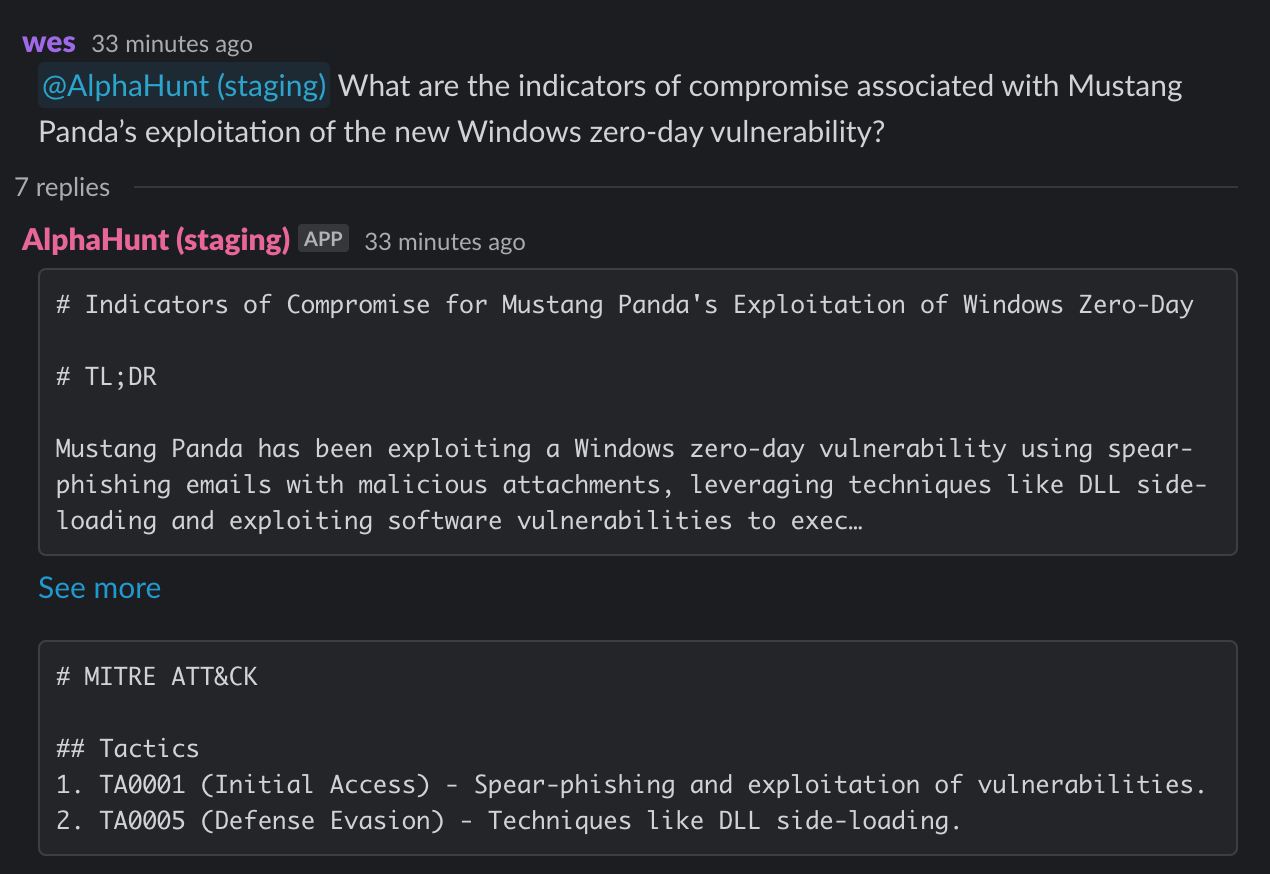
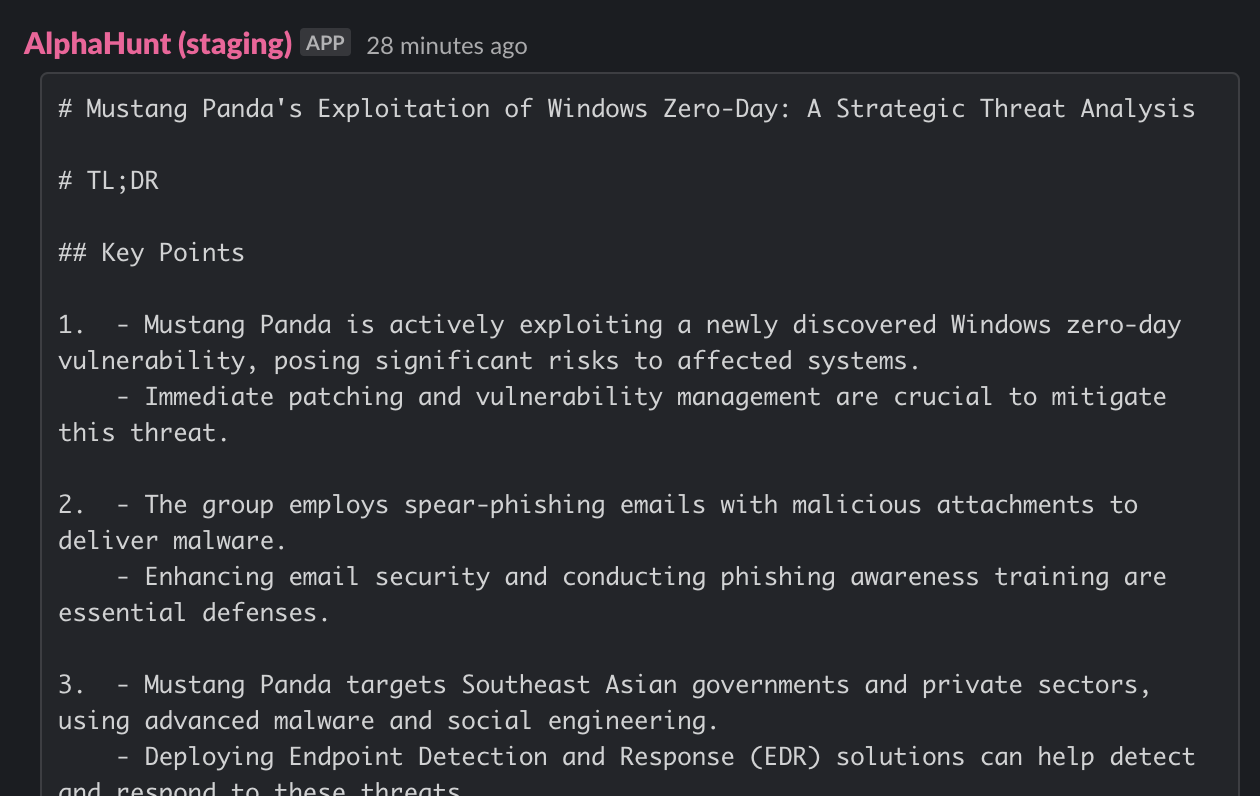
Mustang Panda's Exploitation of Windows Zero-Day: A Strategic Threat Analysis
Mustang Panda, a China-based cyber espionage group, is exploiting a newly discovered Windows zero-day vulnerability to gain unauthorized access to systems. This vulnerability allows the group to execute malicious code...

chat with your team.. and your intel.
EDITOR'S NOTE: I'm testing the next generation of the AlphaHunt- the research goes a bit deeper, a bit more directed and a bit more "peer" reviewed. The layout may still need some work... feedback welcome (just hit reply! :))
Thanks for taking the time to subscribe and read these, if they bring you value, just hit reply and let me know!
TL;DR
Key Points
-
- Mustang Panda is actively exploiting a newly discovered Windows zero-day vulnerability, posing significant risks to affected systems.
- Immediate patching and vulnerability management are crucial to mitigate this threat.
-
- The group employs spear-phishing emails with malicious attachments to deliver malware.
- Enhancing email security and conducting phishing awareness training are essential defenses.
-
- Mustang Panda targets Southeast Asian governments and private sectors, using advanced malware and social engineering.
- Deploying Endpoint Detection and Response (EDR) solutions can help detect and respond to these threats.
-
- Collaboration with other threat actor groups like APT10 and APT41 enhances Mustang Panda's capabilities.
- Engaging in threat intelligence sharing can improve collective defense strategies.
Summary
Mustang Panda, a China-based cyber espionage group, is exploiting a newly discovered Windows zero-day vulnerability to gain unauthorized access to systems. This vulnerability allows the group to execute malicious code, posing a significant threat to targeted organizations, particularly in Southeast Asia. The group uses spear-phishing emails with malicious attachments as a primary method of initial access, leveraging sophisticated social engineering tactics.
To mitigate these threats, organizations should prioritize immediate patching of the identified vulnerability and enhance email security measures. Deploying advanced EDR solutions can provide real-time monitoring and response capabilities, helping to detect and respond to Mustang Panda's tactics. Additionally, conducting regular phishing awareness training for employees can reduce the success rate of spear-phishing campaigns.
Mustang Panda's collaboration with other threat actor groups, such as APT10 and APT41, suggests a broader operational strategy that enhances their capabilities. Engaging with threat intelligence sharing communities can help organizations stay informed about the latest tactics and improve their defense strategies.
In the short term, Mustang Panda is expected to continue exploiting zero-day vulnerabilities and intensifying spear-phishing campaigns. In the long term, the group may expand its targeting beyond Southeast Asia and adopt more advanced evasion techniques to avoid detection. Organizations should remain vigilant and proactive in their cybersecurity efforts to counter these evolving threats.
Indicators of Compromise
-
Indicator 1
- Description: A newly discovered Windows zero-day vulnerability exploited by Mustang Panda, allowing unauthorized access and control over affected systems.
- Source URL: New Microsoft Windows GUI 0-Day Vulnerability Actively Exploited in the Wild
- Confidence: HIGH
- References:
-
Indicator 2
- Description: Mustang Panda's use of spear-phishing emails containing malicious attachments to deliver malware to targeted organizations.
- Source URL: How Mustang Panda collects sensitive intelligence with multi-stage ...
- Confidence: MEDIUM
- References:
Threat Actor Interest
Mustang Panda
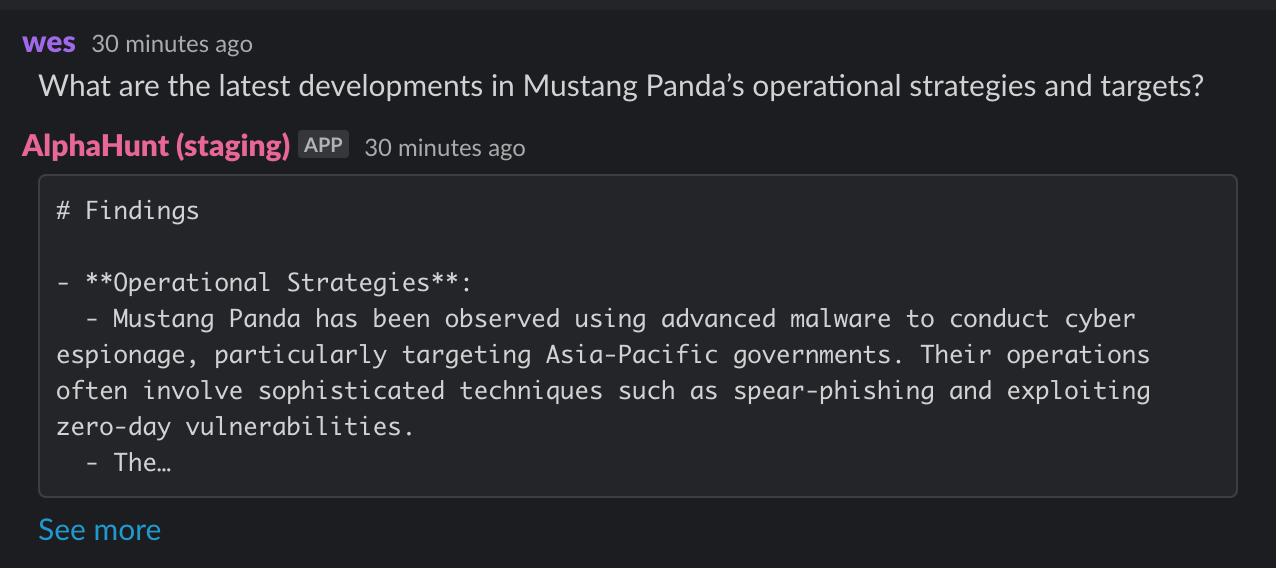
Mustang Panda has shown a keen interest in exploiting zero-day vulnerabilities, particularly in Microsoft Windows systems. Their recent campaigns have targeted Southeast Asian governments and private sector organizations, leveraging advanced malware and spear-phishing techniques to gain access to sensitive information. The malware variants used include custom backdoors and remote access tools that allow for persistent access and data exfiltration.
The group has a history of using sophisticated social engineering tactics, which aligns with their recent activities involving zero-day exploits. This indicates a strategic focus on high-value targets that can yield significant intelligence. Their collaboration with other threat actor groups, such as APT10 and APT41, suggests a broader operational strategy that enhances their capabilities and reach.
- References:
Recommendations, Actions, Suggested Pivots, Forecasts and Next Steps..
(Subscribers Only)


![[DEEP RESEARCH] When Gambling Becomes a Money-Transfer Rail](/content/images/size/w600/2026/03/z-1.png)
![[DEEP RESEARCH] Who’s Most Likely to Abuse MCP Integrations? UNC3944, TraderTraitor, UNC6293](/content/images/size/w600/2026/03/z.png)

![[FORECAST UPDATED] AI Agents as Regulated C2: Will Anyone Be Forced to Act?](/content/images/size/w600/2026/02/z-11.png)