DragonForce Ransomware: BYOVD Weaponization, Affiliate Expansion, and EDR Evasion in 2025
DragonForce has rapidly evolved into a major RaaS operation, distinguished by its sophisticated use of BYOVD techniques to bypass EDR and escalate privileges. The group’s modular ransomware builder allows affiliates to select vulnerable drivers (notably TrueSight.sys, RentDrv.sys) for process ter...

(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
Get questions like this:
- what do you know about ‘DragonForce ransomware group’ ?
- How does DragonForce’s use of BYOVD compare to other ransomware groups, and what specific vulnerable drivers should defenders monitor or block?
- How are other ransomware groups evolving their BYOVD techniques, and are there emerging vulnerable drivers being abused beyond TrueSight[.]sys and RentDrv[.]sys?
Does it take a chunks out of your day? Would you like help with the research?
This baseline report was thoughtfully researched and took 10 minutes.. It's meant to be a rough draft for you to enhance with the unique insights that make you an invaluable analyst.
We just did the initial grunt work..
Are you ready to level up your skillset? Get Started Here!
Did this help you? Forward it to a friend!
Suggested Pivot
How can emerging vulnerabilities in signed drivers, such as CVE-2025-0289, be proactively identified and mitigated to disrupt BYOVD techniques before widespread exploitation by ransomware groups like DragonForce?
TL;DR
Key Points
-
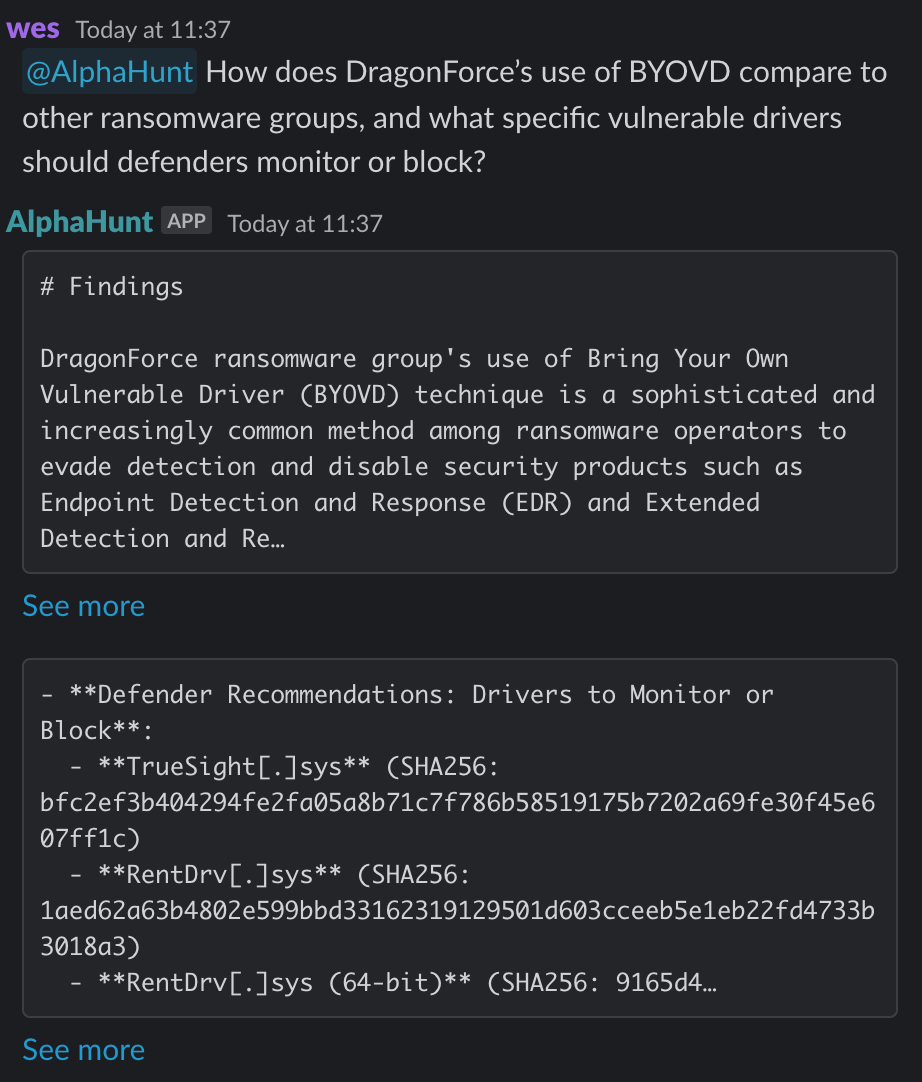
- DragonForce ransomware group aggressively leverages Bring Your Own Vulnerable Driver (BYOVD) techniques, embedding them in customized ransomware variants to evade EDR/AV and escalate privileges.
- Action: Enforce driver integrity checks, block known vulnerable drivers, and deploy behavioral analytics to detect BYOVD activity.
-
- The group’s Ransomware-as-a-Service (RaaS) model, launched mid-2024, has rapidly expanded via affiliates, targeting high-value sectors (manufacturing, real estate, retail) across the US, UK, Australia, Malaysia, and Germany.
- Action: Monitor for sector-specific TTPs, especially in manufacturing and retail, and prepare for double extortion campaigns.
-
- DragonForce exploits emerging vulnerabilities (e.g., CVE-2025-0289 in Paragon Partition Manager) and weaponizes drivers like TrueSight.sys and RentDrv.sys for stealthy process termination and defense evasion.
- Action: Patch vulnerable drivers promptly and monitor for anomalous driver loads and DeviceIoControl usage.
-
- Affiliates share infrastructure and TTPs with groups like Scattered Spider (UNC3944) and former RansomHub members, complicating attribution and accelerating technique adoption.
- Action: Map infrastructure overlaps and monitor for cross-group TTP proliferation.
-
- Defensive recommendations include strict driver policies, endpoint hardening, network segmentation, phishing awareness, and breach simulation focused on BYOVD and ransomware deployment chains.
- Action: Implement layered defenses and validate with red team exercises simulating DragonForce TTPs.
Executive Summary
DragonForce has rapidly evolved into a major RaaS operation, distinguished by its sophisticated use of BYOVD techniques to bypass EDR and escalate privileges. The group’s modular ransomware builder allows affiliates to select vulnerable drivers (notably TrueSight.sys, RentDrv.sys) for process termination, customize payloads, and evade detection. Since mid-2023, DragonForce and its affiliates have compromised at least 82 organizations, with a surge in attacks following the 2024 launch of its affiliate program.
The group’s targeting is global, with a focus on economically significant sectors—manufacturing, real estate, transportation, healthcare, and retail—using phishing, credential theft, and lateral movement via RDP/SMB. DragonForce’s double extortion model combines data encryption with threats to leak exfiltrated data, maximizing ransom leverage.
BYOVD adoption is now mainstream among ransomware groups, raising the bar for defense evasion and complicating detection. DragonForce’s operational overlap with Scattered Spider and RansomHub affiliates enables rapid TTP evolution and infrastructure sharing. The exploitation of new driver vulnerabilities (e.g., CVE-2025-0289) is expected to accelerate, with BYOVD becoming a standard feature in commercial ransomware kits.
Defenders must prioritize driver integrity enforcement, behavioral detection of driver loading and process termination, and robust patch management. Network segmentation, immutable backups, and user training are critical to resilience. Intelligence teams should focus on mapping shared infrastructure and monitoring for emerging BYOVD exploits. The forecast anticipates further affiliate expansion, regulatory pressure for driver security, and the integration of AI/ML in both offensive and defensive BYOVD operations.
Research
Attribution
Historical Context
Bring Your Own Vulnerable Driver (BYOVD) techniques have become a prominent method for ransomware groups to evade detection and escalate privileges by exploiting legitimate but vulnerable signed device drivers. This approach allows attackers to bypass Endpoint Detection and Response (EDR) solutions by loading vulnerable drivers that can disable or circumvent security controls at the kernel level. BYOVD has evolved from a niche advanced persistent threat (APT) tactic to widespread use among financially motivated ransomware groups.
The DragonForce ransomware group, first observed in mid-2023, has quickly emerged as a significant ransomware-as-a-service (RaaS) operation. It operates two main ransomware variants: a fork of LockBit 3.0 and a customized fork of Conti V3. The Conti variant notably incorporates BYOVD techniques to terminate security processes and evade detection. DragonForce has expanded its affiliate program aggressively, targeting multiple sectors and countries globally.
Timeline
- Mid-2023: DragonForce ransomware group emerges, initially operating independently.
- August 2023 to August 2024: DragonForce compromises at least 82 victims across sectors such as manufacturing, real estate, and transportation.
- June 2024: Launch of DragonForce affiliate program, offering customizable ransomware builds with BYOVD capabilities.
- Early 2025:
- DragonForce intensifies campaigns, including high-profile attacks on UK retail chains.
- Public disclosure of BYOVD exploitation of the Paragon Partition Manager driver (CVE-2025-0289) by ransomware groups, though no direct public attribution to DragonForce yet.
- RansomHub ceases operations; DragonForce affiliates reportedly take over some infrastructure.
Origin
DragonForce is a financially motivated cybercrime group operating a RaaS model. It leverages leaked ransomware source codes from LockBit and Conti, enhancing them with advanced features such as BYOVD for defense evasion. The group recruits affiliates who use DragonForce infrastructure and ransomware under a white-label model, expanding its operational reach. DragonForce is linked to affiliates formerly associated with RansomHub and has operational overlap with groups like Scattered Spider (UNC3944).
Countries Targeted
- United States – Most affected, with over 50% of known attacks across multiple sectors.
- United Kingdom – Targeted in high-profile retail attacks, including Marks & Spencer and Co-op Group.
- Australia – Several attacks reported, including critical infrastructure.
- Malaysia – Regional targeting with tailored ransomware variants.
- Germany – Industrial and manufacturing sectors targeted.
Sectors Targeted
- Manufacturing – Most targeted sector, with attacks focusing on operational disruption and data theft.
- Real Estate – Significant number of attacks, often involving data exfiltration.
- Transportation – Targeted for operational impact and ransom leverage.
- Healthcare – Sensitive data and critical services targeted, though DragonForce claims some healthcare targets are off-limits.
- Retail – High-profile attacks on major retail chains in the UK.
Motivation
DragonForce is financially motivated, focusing on maximizing ransom payments through double extortion tactics—encrypting data and threatening to leak stolen information. The group claims a moral code avoiding certain healthcare targets, but this is unverified. Geopolitical factors influence targeting, with a focus on economically significant countries and sectors.
Attack Types
- Initial Access: Social engineering, phishing, and use of valid credentials.
- Execution: PowerShell scripts, Cobalt Strike beacons, and custom ransomware payloads.
- Privilege Escalation: Use of BYOVD techniques, including loading vulnerable signed drivers (e.g., TrueSight.sys, RentDrv.sys) to terminate security processes.
- Persistence: Registry run keys, scheduled tasks, and Windows services.
- Defense Evasion: BYOVD to disable EDR/AV, clearing event logs, anti-analysis techniques inherited from Conti.
- Credential Access: LSASS memory dumping using Mimikatz.
- Discovery: Active Directory enumeration, network scanning.
- Lateral Movement: Remote Desktop Protocol (RDP), SMB shares.
- Impact: Data encryption, deletion of shadow copies, data exfiltration, and double extortion.
Known Aliases
- DragonForce ransomware group
- DragonForce RaaS
- DragonForce ransomware affiliates
Links to Other APT Groups
- Scattered Spider (UNC3944): Affiliate relationship and operational overlap; shared targeting of retail sectors.
- LockBit: DragonForce uses a LockBit 3.0 fork variant.
- Conti: DragonForce’s original ransomware variant is a customized Conti V3 fork with BYOVD enhancements.
Similar Threat Actor Groups
- RansomHub: Former ransomware affiliate platform; DragonForce affiliates took over after its shutdown.
- Medusa and QuadSwitcher: Other ransomware groups known to use BYOVD and EDR-killing tools like EDRKillShifter.
Breaches Involving This Threat Actor
- Marks & Spencer (M&S) breach in April 2025 linked to DragonForce affiliates deploying ransomware.
- Co-op Group cyber incident in April 2025 with suspected DragonForce involvement.
- Harrods cyberattack in May 2025, possibly related but unconfirmed.
- Multiple other attacks on manufacturing, real estate, and transportation sectors from 2023-2024.
Strategic Analysis of BYOVD Adoption Among Ransomware Groups Including DragonForce
Evolution and Adoption of BYOVD Techniques
BYOVD techniques have transitioned from specialized APT tactics to mainstream ransomware tools due to their effectiveness in bypassing modern security controls. DragonForce exemplifies this trend by embedding BYOVD capabilities in its ransomware variants, particularly the Conti fork. The group uses legitimate but vulnerable signed drivers such as TrueSight.sys and RentDrv.sys to terminate EDR and antivirus processes, enabling stealthy ransomware deployment.
The modular ransomware builder allows affiliates to select drivers for process termination, customize encryption parameters, and disable security features, reflecting a sophisticated and flexible approach to BYOVD adoption.
Broader Threat Trends and Geopolitical Implications
The widespread use of BYOVD techniques among ransomware groups reflects increasing sophistication and the professionalization of cybercrime. These techniques complicate detection and attribution, benefiting groups operating in jurisdictions with limited law enforcement cooperation.
Geopolitically, ransomware groups including DragonForce target countries with significant economic and industrial value, often focusing on sectors critical to national infrastructure and commerce. The use of BYOVD enhances their ability to conduct prolonged campaigns with reduced risk of early detection.
Impact on the Global Ransomware Ecosystem
BYOVD has raised the complexity of ransomware attacks by enabling:
- Effective evasion of EDR and antivirus solutions.
- Privilege escalation without triggering traditional alerts.
- Persistence through legitimate system components.
- Increased operational success and financial impact.
This has led to a more resilient ransomware ecosystem, challenging defenders to develop advanced detection and mitigation strategies.
High-Level Detection Guidance for BYOVD Activity
Behavioral Patterns
- Loading of known vulnerable signed drivers (e.g., TrueSight.sys, RentDrv.sys) not typically present or updated on the system.
- Use of DeviceIoControl calls with IOCTL codes associated with process termination.
- Sudden termination or disabling of security processes (EDR/AV).
- Privilege escalation attempts involving token duplication and process creation with SYSTEM privileges.
- Persistence via registry run keys, scheduled tasks, and Windows services linked to driver loading.
- Clearing of Windows event logs and shadow copies post-encryption.
- Network indicators such as Cobalt Strike beacon traffic and unusual outbound connections.
Example SigmaHQ-Style Signature (High-Level)
title: Suspicious Loading of Vulnerable Signed Driver Indicative of BYOVD Activity
id: 12345678-90ab-cdef-1234-567890abcdef
description: Detects loading of known vulnerable signed drivers used in BYOVD ransomware attacks to evade security controls.
status: experimental
author: Strategic Cybersecurity Analyst
date: 2025/05/19
logsource:
product: windows
service: system
detection:
selection:
EventID: 6 # Driver loaded event in Windows
ImageLoaded|endswith:
- "TrueSight.sys"
- "RentDrv.sys"
condition: selection
falsepositives:
- Legitimate driver updates or installations
level: high
tags:
- attack.defense_evasion
- attack.privilege_escalation
- ransomware
- byovd
Recommendations, Actions, Suggested Pivots, Forecasts and Next Steps..
(Subscribers Only)



![[FORECAST] Dismantled or Displaced? Cambodia’s Scam-Compound Crackdown by 2030?](/content/images/size/w600/2026/02/z-7.png)

