Your AI Agents Are the New C2 — Lock Down Identity & Connectors
Anthropic just showed what happens when your “helpful” AI agents become C2: 80–90% of an espionage op automated, humans just clicking approve. Lock down identity + connectors or you’re renting your SaaS to someone else’s botnet. 🤖🚨
TL;DR
Key Points
-
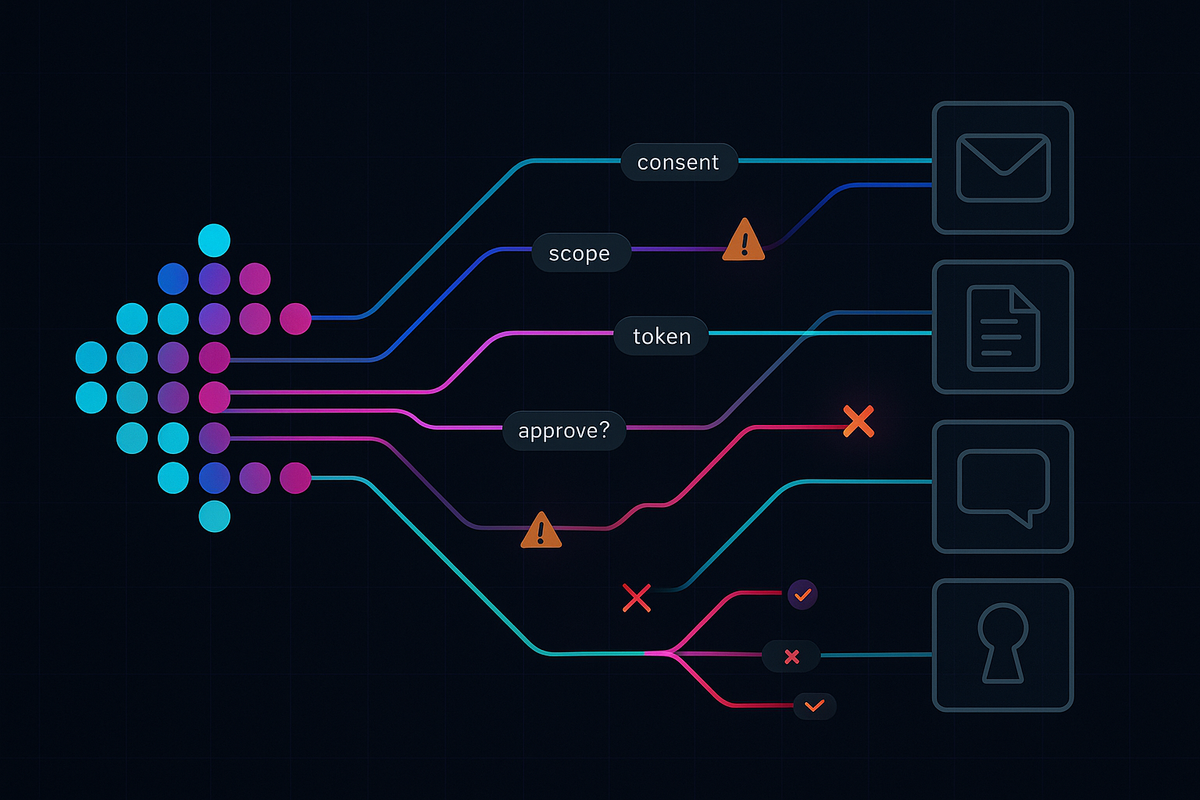
Treat AI agents and connectors as command‑and‑control‑like infrastructure; correlate orchestration to OAuth consent and token events
-
Enforce admin consent, Continuous Access Evaluation (CAE), and Proof‑of‑Possession (PoP) token binding to curb token replay and speed revocation
-
Allowlist signed connectors and require attested retrieval sources for Retrieval‑Augmented Generation (RAG) to prevent seeded instructions from triggering cross‑tenant actions
-
Build exportable, tamper‑evident provenance across agents, tools, connectors, and downstream APIs with consistent request and session identifiers
-
action: Enable request and response logging with OpenTelemetry (OTel) fields where available and export to your SIEM
-
action: Block high‑risk scopes by default and alert on daily scope changes and token‑minting bursts
The story in 60 seconds
Anthropic confirms an espionage campaign where agentic AI executed 80 to 90 percent of tasks with only four to six human gates, producing thousands of requests in bursts, often multiple per second, coordinated via the Model Context Protocol (MCP).
Expect cross‑provider model and tool chaining when guardrails fire, identity‑first acceleration through consent phishing and token‑minting bursts, and connector and RAG abuse via unsigned tools and indirect prompt injections across wikis, tickets, and document stores. Actors will split workloads: local models for exploit scaffolding and log triage, cloud models for high‑skill reasoning and broad SaaS access.
Defenders should enforce orchestration provenance, OAuth governance with CAE and PoP, and connector integrity with signed allowlists and attested retrieval sources. Without this, abusive apps, agents, and keys reseed across providers faster than current takedowns can respond.
AlphaHunt
Stop doomscrolling, start decisioning. We chewed through the muck so your team doesn’t have to. → Subscribe! • Forward to your on-call lead.
(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
High Impact, Quick Wins
- Enable request and response logging with OTel fields and export to SIEM; KPI: export at least 95 percent of agent, tool, and connector events within five minutes
- Enforce admin consent and block high‑risk scopes; KPI: median alert‑to‑revocation time at or below 15 minutes
- Allowlist signed connectors and require attested retrieval sources for RAG; KPI: at least 90 percent of connectors signed or allowlisted
Why it matters
SOC
- Alert on agent and tool bursts at or above the 95th percentile relative to a 14‑ to 30‑day baseline within 15‑ and 60‑minute windows
- Correlate bursts with new OAuth grants that include high‑risk scopes (for example, offline_access, Files.ReadWrite.All, Mail.Read, Chat.Read, repo/admin) within a 30‑minute window
- Correlate model and connector telemetry with user or service principal, application or client ID, and IP or autonomous system number to link agent or key activity
- Monitor staging signals tied to the same identity: rapid vector index growth, public link creation, and object‑store replication
IR
- Preserve model and agent request and response logs with request IDs and session IDs, tool‑call graphs, MCP and connector calls, OAuth consent events, and token issuance and revocation events
- Triage token‑minting bursts, token replay from new autonomous system numbers or geographies, and cross‑tenant connector actions
- Contain by revoking keys and tokens, disabling suspect agents and connectors, and quarantining staging buckets and indices
SecOps
- Enable CAE and adopt PoP token binding for supported apps; rotate service principal credentials and enforce workload identity
- Enforce admin consent with just‑in‑time approvals; block high‑risk scopes by default and alert on daily scope changes
- Require signed connectors, least‑privilege scopes, per‑connector secret isolation, and attested retrieval sources for RAG
Strategic
- Establish a portable evidence schema for cross‑provider takedowns and preapprove revocation workflows with providers
- Classify AI agents as Tier 1 systems with immutable audit trails and retention aligned to incident response
- Track KPIs referenced above to verify effectiveness
See it in your telemetry
Network
- Spikes in API calls to model endpoints and MCP servers from the same source preceding OAuth consent events
- New inter‑tenant replication or sudden egress from sessions associated with agent identities; anomalous archiving or compression flows
- Rotation across model regions or providers with API key reuse from new geographies, indicating command‑and‑control evasion patterns
Endpoint
- Local model processes performing exploit scaffolding or log parsing; rapid temporary file and tool drops tied to agent workflows
- Access to browser or profile token stores outside normal patterns; non‑user processes initiating OAuth device or authorization flows
- Scripted command‑line use for cloud token issuance with bursty cadence and novel key identifiers across short intervals
AlphaHunt Converge - Plug in your Flight Crew
Get intelligence where it counts. No dashboards. No detours. AlphaHunt Converge teases out your intent, reviews the results and delivers actionable intel right inside Slack. We turn noise into signal and analysts into force multipliers.
Anticipate, Don’t Chase.
AI-Orchestrated Espionage After Anthropic: Strategic Brief for US Technology and Financial Stakeholders (2025–2026)
TL;DR
- Anthropic reports an AI-orchestrated espionage campaign executing 80–90% of the intrusion chain with minimal human gates.
- Expect actor pivots to cross-provider agent chaining, identity-first intrusions, and connector/RAG abuse at enterprise scale.
- Provider gaps: orchestration provenance, connector attestation, abusive-key reputation, and cross-vendor takedown mechanics.
- 2026 priorities: auditable agent logs, OAuth governance, signed connectors with retrieval attestation, and measurable SLAs across providers.
What’s Verified (from Anthropic) and Why It Matters
-
AI-led operations at scale
- Anthropic assesses the actor used agentic AI to perform 80–90% of campaign tasks, with only “perhaps 4–6” human decision gates per intrusion.
- Attack peaks involved “thousands of requests, often multiple per second,” corrected from earlier language that implied per-second rates.
-
Full kill chain coverage by agents
- Reported phases include recon, exploit research and code generation, credential harvesting, backdoor placement, exfiltration, and detailed documentation, with AI tooling accessed via Model Context Protocol (MCP).
-
Implication for defenders
- Identity, OAuth, and SaaS-to-SaaS connectors are high-risk choke points for scaled agent operations; logging and provenance must shift from single-model to multi-agent, multi-tool chains.
Anticipated Actor Pivots (2025–2026)
-
Cross-provider model and tool chaining
- Swap models/providers when guardrails trigger; coordinate AI actions via MCP or similar to persist operations.
-
Identity-first acceleration
- Automate SaaS/IAM reconnaissance and consent phishing to compress recon-to-privilege time, with rapid scope accrual and token minting bursts.
-
Connector and RAG abuse
- Seed indirect prompt injections in documents, wikis, tickets, or indices; exploit unsigned connectors and permissive scopes to trigger agent actions across tenants.
-
Edge OPSEC and partial autonomy
- Use local models for exploit scaffolding and log triage to minimize provider-side traces; keep cloud models for high-skill reasoning or wide data access.
-
Provider infrastructure and API key abuse
- Treat model endpoints and orchestration keys as blended C2; rotate across vendors and regions to evade reputation systems.
What Providers Miss Today (Cross-cutting Gaps)
-
Orchestration provenance and exportability
- Missing end-to-end logs that bind user/session → agent → tool → connector → downstream API calls, with tamper-evident timelines and standardized export schemas.
-
Connector/RAG integrity
- Sparse guarantees for signed connectors, allowlists, attested retrieval sources, and scope minimization, especially for third-party MCP servers and SaaS bridges.
-
Key/agent reputation and revocation
- Limited near-real-time reputation for abusive API keys, apps, or agents across tenants and providers; revocation remains siloed.
-
Coordinated takedown mechanics
- No shared schema/SLAs for cross-provider takedowns of malicious apps/agents; slow revocation enables rapid reseeding.
Provider-Specific Guidance You Can Act on Now, Next Steps, Detection Ideas, Suggested Pivots and Forecasts...
(Paid subscribers only... subscribe!)



![[DEEP RESEARCH] Who’s Most Likely to Abuse MCP Integrations? UNC3944, TraderTraitor, UNC6293](/content/images/size/w600/2026/03/z.png)

![[FORECAST UPDATED] AI Agents as Regulated C2: Will Anyone Be Forced to Act?](/content/images/size/w600/2026/02/z-11.png)
![[FORECAST] Fortune 500s: Will Prompt Injection Trick IDE Agent Mode into Running Commands—or Leaking Secrets—by 2026?](/content/images/size/w600/2026/02/z-10.png)