
weekly
SIGNALS WEEKLY: React2Shell in the Wild, BRICKSTORM in the Walls, Predator on the Phone
React2Shell in the wild, BRICKSTORM in the walls, Predator on the phone. Not a dystopian haiku—this week’s risk stack. 🧯🕳️📱

weekly
React2Shell in the wild, BRICKSTORM in the walls, Predator on the phone. Not a dystopian haiku—this week’s risk stack. 🧯🕳️📱

oauth
2026’s nastiest SaaS breaches will ride valid tokens + “trusted” apps. We already got the trailer with the Salesloft/Drift OAuth blast radius. And the browser? Yeah, it’s part of the perimeter now. 😬🔑💬

forecasts
Will hackers actually turn off a city’s water, or is that just conference-slide horror fiction? 💧🤔 We put a number on it...

weekly
🚨 CodeRED alerts ransomed. 🐛 Shai Hulud 2.0 looting CI/CD secrets. 📱 107 Android bugs + Albiriox on-device fraud. Signals Weekly on what to fix first.

ai
Your “normal” AI traffic can be stealth C2 now. Dark LLMs are writing per-host pwsh one-liners, self-rewriting droppers, and hiding in model APIs you approved. If you’re not policing AI egress, you’re not doing detection. 😬🤖

weekly
Wormed npm repos. Multi-vector APTs. KEV-listed identity RCE. If your CI/CD + SSO aren’t on the same crisis board this week, you’re already late. 😈🚨
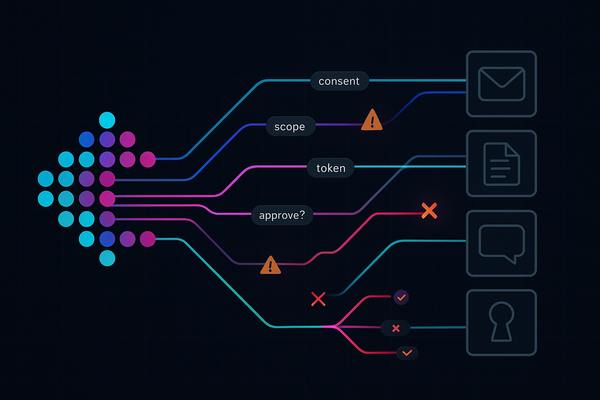
ai
Anthropic just showed what happens when your “helpful” AI agents become C2: 80–90% of an espionage op automated, humans just clicking approve. Lock down identity + connectors or you’re renting your SaaS to someone else’s botnet. 🤖🚨

forecasts
20% odds Akira triggers a 7-day ambulance diversion at a 10+ hospital system by end of 2026. 🚑 Still feeling “low risk”?

weekly
A Chinese crew let a jailbroken AI run most of the intrusion while FortiWeb + Firebox burn in KEV and a contractor leak drops the playbook.

cl0p
LockBit got the Operation Cronos takedown. BlackCat imploded. Cl0p just logged a record leak month—and shows no sign of slowing. By 2026, do we really keep Cl0p dark for 90+ days… or just get Cl0p v2 with a fresh logo?

unc6485
UNC6485 is farming Triofox: Host: localhost → setup → mint admin → AV path = your script → SYSTEM → RMM + reverse RDP/443. Patch to 16.7.10368.56560 now. Copycats next. 🔥🛡️
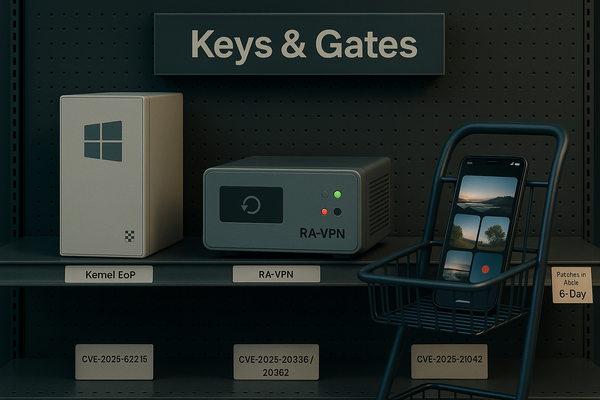
weekly
Keys. Gates. Windows. Actively exploited Win kernel EoP ✅ (CVE-2025-62215). Cisco RA-VPN bugs can reload unpatched edges. LANDFALL used Samsung’s image bug (CVE-2025-21042). Which breaks first in your shop?