Hypervisor Ransomware: CVE-2024-37085, AD Abuse, and the Escalating Threat to VMware ESXi Environments
Ransomware groups—including BlackCat/ALPHV, Black Basta, RansomHub, and Dark Angels—are increasingly targeting VMware ESXi and similar virtualization platforms using advanced hypervisor-level attack techniques. The exploitation of CVE-2024-37085..

(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
Have a ESXi Environment- not sure what these headlines mean??
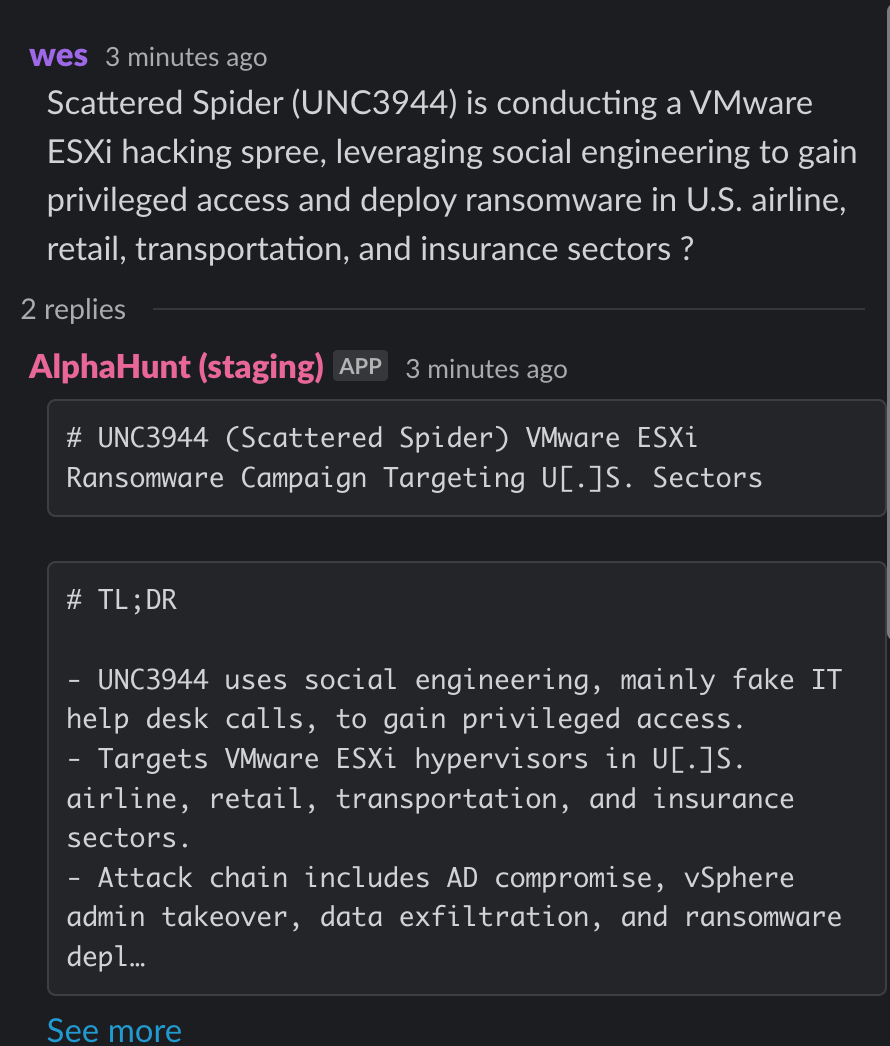
- Scattered Spider (UNC3944) is conducting a VMware ESXi hacking spree, leveraging social engineering to gain privileged access and deploy ransomware in U.S. airline, retail, transportation, and insurance sectors ?
Does it take a chunks out of your day? Would you like help with the research?
This baseline report was thoughtfully researched and took 10 minutes.. It's meant to be a rough draft for you to enhance with the unique insights that make you an invaluable analyst.
We just did the initial grunt work..
Are you ready to level up your skillset? Get Started Here!
Did this help you? Forward it to a friend!
you're still surfing RSS feeds? put the latest news, insights and intel, straight into your knowledge graph.
TL;DR
Key Points
-
- Ransomware groups are exploiting CVE-2024-37085 and Active Directory misconfigurations to gain hypervisor-level control over VMware ESXi, enabling mass encryption and operational disruption.
- Immediate patching, AD group management hardening, and network segmentation are critical to mitigate these attacks.
-
- Attackers leverage credential theft, lateral movement tools (Cobalt Strike, SystemBC), and social engineering (notably by UNC3944/Scattered Spider) to escalate privileges and deploy Linux-based ESXi encryptors.
- Enforcing phishing-resistant MFA, immutable backups, and real-time monitoring is essential for resilience and rapid response.
-
- Code reuse (Babuk leak), affiliate collaboration, and double-extortion tactics are accelerating ransomware evolution across critical infrastructure, manufacturing, healthcare, finance, and technology sectors.
- Organizations must adopt layered defense strategies and monitor for anomalous AD and hypervisor activity.
Executive Summary
Ransomware groups—including BlackCat/ALPHV, Black Basta, RansomHub, and Dark Angels—are increasingly targeting VMware ESXi and similar virtualization platforms using advanced hypervisor-level attack techniques. The exploitation of CVE-2024-37085, which allows attackers to create or rename an "ESX Admins" group in Active Directory and gain full administrative access to ESXi hosts, is a critical vector. Attackers combine this with credential theft (Mimikatz/Pypykatz), lateral movement (Cobalt Strike, SystemBC), and backup destruction to maximize impact and enable double-extortion.
Distinctive TTPs include the use of Linux-based ESXi encryptors (often derived from Babuk source code), SSH tunneling, and esxcli commands for payload deployment. Social engineering remains a key access vector, especially for UNC3944/Scattered Spider, which specializes in help desk impersonation and SIM swapping.
Sectoral targeting is broad, with critical infrastructure, manufacturing, healthcare, finance, and technology organizations at heightened risk. Defensive gaps—such as unpatched ESXi hosts, over-permissive AD group management, lack of MFA, and insufficient network segmentation—are routinely exploited.
Recommended mitigations include immediate patching of CVE-2024-37085, hardening AD group management, enforcing phishing-resistant MFA, segmenting management networks, deploying SIEM/XDR for real-time monitoring, and maintaining immutable, isolated backups. Organizations should also invest in security awareness training and incident response planning to counter evolving ransomware tactics.
Forecasts indicate continued escalation of hypervisor-level ransomware attacks, with new variants, increased affiliate collaboration, and the likely adoption of AI-enhanced social engineering and evasion techniques. Proactive, layered defense and continuous monitoring are essential to mitigate these evolving threats.
Deep Technical Analysis of Ransomware Groups Adopting Hypervisor-Level Attack Techniques Against VMware ESXi and Comparable Virtualization Platforms
1. Initial Access Vectors and Privilege Escalation Methods
- Ransomware groups such as BlackCat/ALPHV, Black Basta, RansomHub, and Dark Angels gain initial access primarily through phishing campaigns, malware infections (e.g., Qakbot), exploitation of vulnerabilities in exposed management interfaces, and abuse of Active Directory (AD) permissions.
- Privilege escalation is often achieved by exploiting vulnerabilities in ESXi hypervisors joined to AD domains, such as CVE-2024-37085, which allows attackers to create or rename a domain group named "ESX Admins," granting full administrative access to ESXi hosts.
- Attackers also use credential theft tools like Mimikatz or its Python variant Pypykatz, lateral movement tools such as Cobalt Strike, and persistence implants like SystemBC.
- Social engineering remains a key tactic for groups like UNC3944 (Scattered Spider), which use SMS phishing, SIM swapping, and impersonation of help desk personnel to gain access.
2. Technical Mechanisms for Targeting Hypervisors
- Exploitation of CVE-2024-37085 is a critical vector: VMware ESXi hypervisors joined to AD domains grant full administrative access to any member of a domain group named "ESX Admins" without validating the group's existence or security identifier (SID).
- Threat actors create this group and add themselves to it, gaining full control over the hypervisor.
- Attackers use esxcli commands and SSH tunneling to deploy ransomware payloads and encrypt the ESXi file system, rendering hosted virtual machines inoperable.
- Backup destruction or encryption is common to prevent recovery.
- Data exfiltration is used for double-extortion tactics.
- Lateral movement to non-virtualized systems is also observed.
3. Distinctive TTPs Compared to UNC3944 (Scattered Spider)
| Group | Initial Access & Privilege Escalation | Hypervisor Targeting Techniques | Distinctive TTPs Compared to UNC3944 |
|---|---|---|---|
| UNC3944 | Social engineering (SMS phishing, SIM swapping), help desk impersonation | Less focus on direct hypervisor exploits; uses social engineering to gain access | Heavy use of social engineering and telephone-based tactics; less direct exploitation of hypervisor vulnerabilities |
| BlackCat/ALPHV | Malware infections, exploitation of vulnerabilities, credential theft | Linux-based ESXi encryptors, exploitation of AD misconfigurations | Use of Linux encryptors for ESXi, direct exploitation of CVE-2024-37085, broader ransomware toolkit |
| Black Basta | Malware infections (Qakbot), lateral movement with Cobalt Strike | Exploitation of CVE-2024-37085, creation of ESX Admins group | Use of advanced post-exploitation tools, persistence implants, and backup destruction |
| RansomHub | Affiliate operations, social engineering, malware infections | Similar hypervisor targeting as BlackCat, use of Linux encryptors | Collaboration with other groups, shared operational playbooks |
| Dark Angels | Malware infections, exploitation of vulnerabilities | ESXi-specific ransomware variants, backup destruction | Escalated scale and ransom demands, refined hypervisor targeting |
4. Overlap in Toolsets, Code Reuse, or Operational Playbooks
- Babuk ransomware source code leak influenced the development of Linux-based ESXi encryptors used by BlackCat and others.
- Common use of tools like AnyDesk, TeamViewer for remote access, Cobalt Strike for lateral movement, and credential theft tools (Mimikatz/Pypykatz).
- Shared exploitation of AD group misconfigurations and centralized identity systems.
- Double-extortion playbooks involving data exfiltration and backup destruction are common.
- Collaboration and affiliate relationships exist, e.g., UNC3944 was a RansomHub affiliate, and DragonForce ransomware operators claimed control of RansomHub.
5. Documented Incident Timelines and Sectoral Targeting
- Timeline:
- 2021: Babuk and LockBit introduce ESXi-specific encryptors.
- Late 2021-2022: BlackCat, Black Basta, DarkSide, and REvil develop hypervisor-specific variants.
- 2023: Scattered Spider cripples over 100 hypervisors; Dark Angels and RansomHub escalate tactics.
- 2024: New families like Play, Eldorado, and SEXi continue the trend.
- 2024 (Microsoft observed): Storm-0506 used CVE-2024-37085 to deploy Black Basta ransomware in a North American engineering firm.
- Sectoral Targeting:
- Critical infrastructure, manufacturing, healthcare, finance, government, telecommunications, retail, and technology sectors.
- UNC3944 targets telecommunications, financial services, retail, and technology sectors, often focusing on large enterprises with outsourced IT.
- Retail organizations increasingly targeted for their PII and financial data.
6. Defensive Gaps Exploited and Technical Mitigations Recommended
(Subscribe to see more!)
Recommendations, Actions, Suggested Pivots, Forecasts and Next Steps
(Subscribers Only)


![[DEEP RESEARCH] Who’s Most Likely to Abuse MCP Integrations? UNC3944, TraderTraitor, UNC6293](/content/images/size/w600/2026/03/z.png)

![[FORECAST UPDATED] AI Agents as Regulated C2: Will Anyone Be Forced to Act?](/content/images/size/w600/2026/02/z-11.png)
![[FORECAST] Fortune 500s: Will Prompt Injection Trick IDE Agent Mode into Running Commands—or Leaking Secrets—by 2026?](/content/images/size/w600/2026/02/z-10.png)