ClickFix to Linked-Device Takeovers: Will Star Blizzard Introduce a New Initial-Access Vector by Oct 2026?
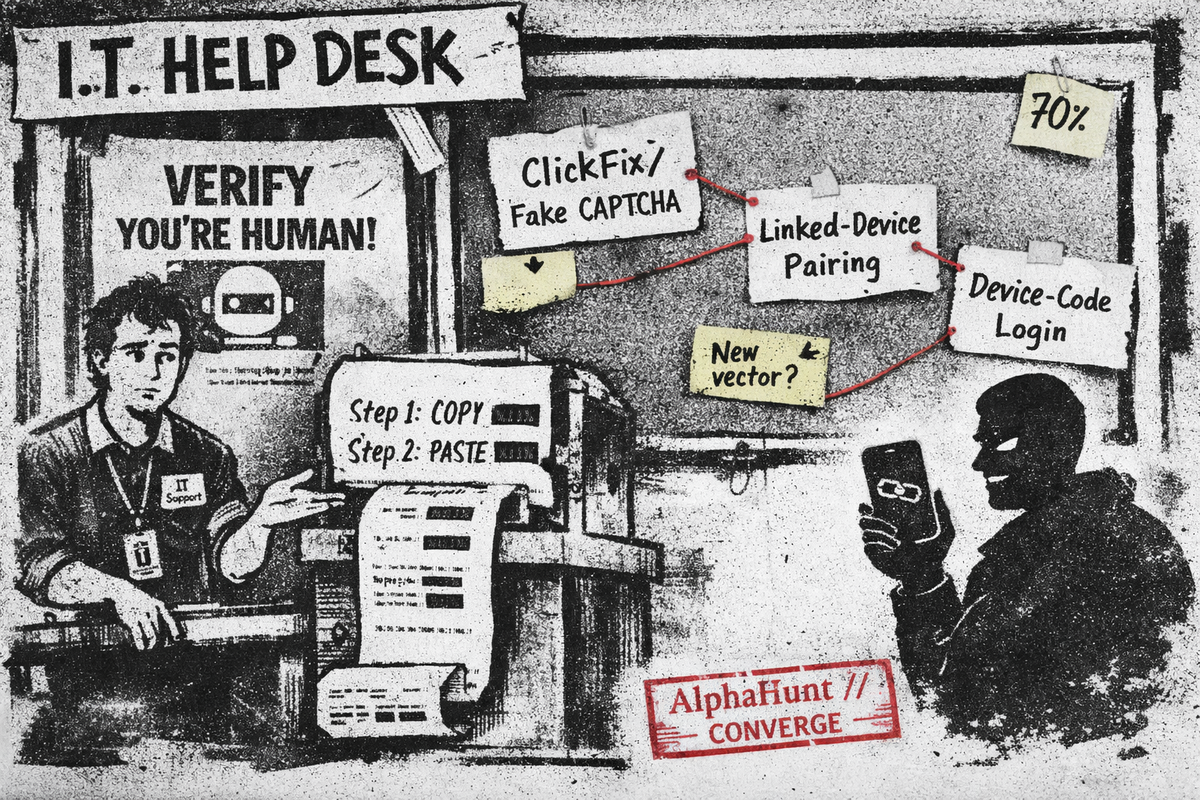
Fake CAPTCHA ➜ “paste this PowerShell.” 🙃 Linked-device pairing ➜ quiet account takeovers. 👻 Device-code phishing ➜ legit login page, attacker gets tokens. 🔑
Checkout the original forecast first: ColdRivers Next Move...
TL;DR
Question
By 2026-10-21, will a top-tier source (Google TAG/GTI, Microsoft Threat Intelligence, UK NCSC, CISA, Zscaler, or Mandiant) publicly attribute to COLDRIVER (aka Star Blizzard/SEABORGIUM/UNC4057/Callisto) either: (A) a new custom malware family, or (B) a materially new initial-access vector, beyond those documented as of 2025-10-21?
Executive Forecast
There is a 70% chance that by 21 October 2026 at least one major vendor will credit COLDRIVER with either a genuinely new malware family or a clearly new access class (beyond SPICA/LOSTKEYS/ROBOT and WhatsApp/Signal linked-device abuse). The main upside driver is COLDRIVER’s demonstrated pattern of retooling when exposed; the main downside driver is a recent period of relative stability. A vendor blog tomorrow tying COLDRIVER to a new messenger/OAuth flow or a distinct Rust/Go/Python backdoor would push me toward ~80–85%; another 6+ quiet months or a credible disruption action would pull me down toward ~50%.
AlphaHunt
Stop doomscrolling, start decisioning. We chewed through the muck so your team doesn’t have to. → Subscribe!
Like this? Forward this to a friend!
(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
Forecast Card
-
Question: By 2026-10-21, will a top-tier source (Google TAG/GTI, Microsoft Threat Intelligence, UK NCSC, CISA, Zscaler, or Mandiant) publicly attribute to COLDRIVER (aka Star Blizzard/SEABORGIUM/UNC4057/Callisto) either: (A) a new custom malware family, or (B) a materially new initial-access vector, beyond those documented as of 2025-10-21?
-
Resolution Criteria:
- Source scope: A public blog/report/advisory from at least one of: Google TAG/GTI, Microsoft Threat Intelligence, UK NCSC, CISA, Zscaler, or Mandiant.
- Attribution: The document must explicitly attribute the activity/tooling to COLDRIVER / Star Blizzard / SEABORGIUM / UNC4057 / Callisto with ≥ “moderate” confidence (or equivalent phrasing).
- (A) New custom malware family (Yes if):
- Malware is new-to-COLDRIVER and not publicly reported as COLDRIVER tooling by any listed source on or before 2025-10-21.
- Clear evidence of a distinct codebase/behavior, such as at least one of:
- New C2 protocol or framing, or
- New implementation language, loader architecture, or backdoor design, or
- Non-trivial new functionality (e.g., different collection/persistence model), beyond compiler/packer/obfuscator/config-only changes.
- Explicitly excluded:
- Renames/repacking; C2/domain/URL swaps; minor obfuscation;
- Configuration-only or string changes;
- Thin loaders with ≥70% code reuse of SPICA, LOSTKEYS, NOROBOT/YESROBOT/MAYBEROBOT, BAITSWITCH/SIMPLEFIX.
- (B) Materially new initial-access vector (Yes if):
- A new class of initial access for COLDRIVER, such as:
- Abuse of a previously unused messenger or communication platform;
- A new SaaS/OAuth/device-code/linked-device flow;
- A qualitatively different human-in-the-loop compromise mechanism (e.g., device linking, consent-grant phishing) vs. “enter password on fake login page.”
- Explicitly excluded:
- New lure themes with the same email credential-phish flow;
- Cosmetic HTML/UX tweaks to existing ClickFix-style pages;
- Phishing-kit reskins on already-used platforms (email, WhatsApp linked-device, Signal linked-device) without a new compromise mechanism.
- A new class of initial access for COLDRIVER, such as:
- Baseline COLDRIVER tooling/vectors (pre-2025-10-21; do not count as “new”):
- 2022–2023: email-centric spear-phishing + EvilGinx AiTM credential theft; no custom malware/vectors reported for COLDRIVER/Star Blizzard.[^ms-2022] [^cisa-2023]
- SPICA Rust backdoor via encrypted-PDF “decryptor” utilities (first custom COLDRIVER malware family).[^lostkeys]
- LOSTKEYS VBS document-theft malware + ClickFix fake-CAPTCHA PowerShell chain.[^lostkeys]
- ROBOT family – NOROBOT downloader, YESROBOT Python backdoor, MAYBEROBOT PowerShell backdoor – delivered via updated ClickFix (“COLDCOPY”) lures.[^robot]
- WhatsApp linked-device abuse for account takeover (Star Blizzard).[^ms-whatsapp]
- Signal linked-device abuse within multi-actor Russia-aligned ecosystem, explicitly including COLDRIVER/Star Blizzard among actors.[^signal]
- Outcome: Resolves Yes if ≥1 qualifying (A) or (B) event is published by a listed source by end of day 2026-10-21 (America/New_York). Otherwise No.
-
Horizon: 2026-10-21 (America/New_York)
-
Probability (Now): 70% | Log-odds: 0.85
-
Confidence in Inputs: Medium
AlphaHunt Converge - Plug in your Flight Crew
Get intelligence where it counts. No dashboards. No detours. AlphaHunt Converge teases out your intent, reviews the results and delivers actionable intel right inside Slack. We turn noise into signal and analysts into force multipliers.
Anticipate, Don’t Chase.




![[FORECAST UPDATED] AI Agents as Regulated C2: Will Anyone Be Forced to Act?](/content/images/size/w600/2026/02/z-11.png)
![[FORECAST] Fortune 500s: Will Prompt Injection Trick IDE Agent Mode into Running Commands—or Leaking Secrets—by 2026?](/content/images/size/w600/2026/02/z-10.png)
