Cl0p’s Leak Sites: 20% Chance They Go Dark by Apr 22, 2026
Forecast: 20% chance Cl0p’s leak sites go dark by Apr 22, 2026. Needs a seizure banner or ≥14 days down w/ LE attribution. Cronos showed it’s doable; mirrors make it brutal.
Executive Overview
Forecast Question
Will a coordinated law enforcement operation disrupt Cl0p’s extortion infrastructure within the next six months?
Resolution
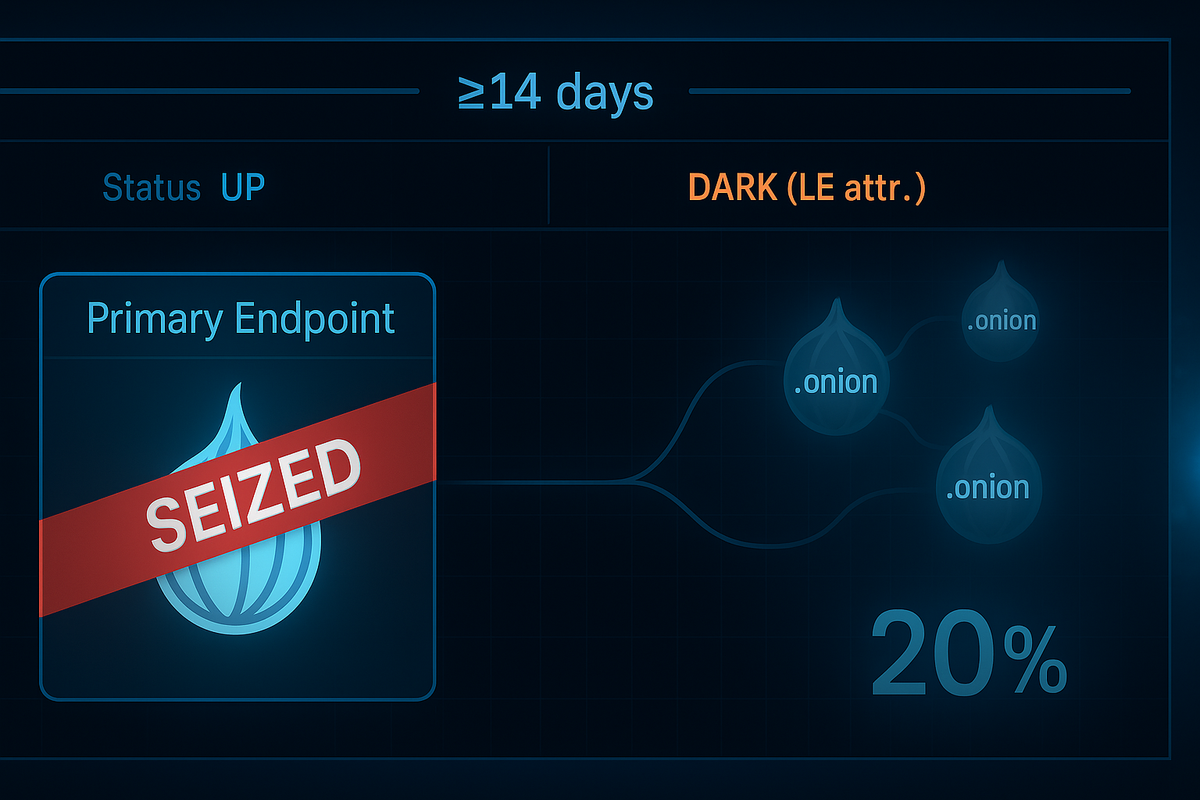
There is a 20% chance that coordinated law enforcement will measurably disrupt Cl0p’s extortion endpoints within six months. Multi-country takedowns (ALPHV 2023, LockBit 2024 actions, 8Base/Phobos 2025) show rising LE capability. However, Cl0p’s centralized, data-theft model, jurisdictional challenges, and ability to mirror sites temper odds. Watch for Europol/DOJ/NCA naming Cl0p, verified seizure banners on Cl0p’s Tor DLS/portals, or a sustained ≥14-day outage with official LE attribution.
AlphaHunt
Stop doomscrolling, start decisioning. We chewed through the muck so your team doesn’t have to. → Subscribe! • Forward to your on-call lead.
(Have feedback? Did something resonate with you? Did something annoy you? Just hit reply! :))
Forecast Card
Question
Will a coordinated law enforcement operation disrupt Cl0p’s extortion infrastructure within the next six months?
Resolution
- Resolution Criteria:
- Resolve Yes if, by 2026-04-22 (America/New_York), a coordinated law-enforcement action attributed to at least two agencies from different countries (or one national agency plus Europol/Eurojust) against Cl0p/TA505/FIN11 leads to either:
- A seizure/defacement banner on at least one primary Cl0p extortion endpoint (Tor .onion data leak site or negotiation/payment portal), or
- Sustained inaccessibility (HTTP/SOCKS failure, timeout, or LE-controlled replacement) of all primary Cl0p data leak sites and negotiation/payment portals for ≥14 consecutive days, with an official LE press release within ±7 days stating infrastructure seizure/takedown.
- Definitions and measurement:
- Primary endpoints: the Tor .onion data leak site(s) and negotiation/payment portals, plus any official clearnet proxies/mirrors, that Cl0p referenced in ransom notes or on their main site in the 30 days prior to the event. The “known set” is locked at T0 (the day before the alleged action) and evidenced via archived ransom notes or reputable trackers (e.g., snapshots preserved for audit).
- LE-claimed: an official agency press release or an on-site seizure banner bearing identifiable agency seals/logos and a verifiable link to an official domain.
- Partial seizures/mirror migration: If ≥1 primary endpoint remains reachable and controlled by Cl0p within 48 hours, criterion (2) is not met; criterion (1) may still resolve Yes if a verified LE seizure banner is present on any primary endpoint.
- Exclusions: Outages without LE attribution (e.g., DDoS, hosting issues), voluntary rebrands/migrations, arrests/sanctions without proven impact on extortion endpoints resolve No.
- Resolve Yes if, by 2026-04-22 (America/New_York), a coordinated law-enforcement action attributed to at least two agencies from different countries (or one national agency plus Europol/Eurojust) against Cl0p/TA505/FIN11 leads to either:
- Horizon: 2026-04-22
- Probability (Now): 20% | Log-odds: -1.39
- Confidence in Inputs: Medium
- Base Rate: 18% from multi-agency disruptions of top ransomware groups over 6-month windows (Hive 2023; RagnarLocker 2023; ALPHV 2023; LockBit 2024; 8Base 2025). Reference class: top 5 crews (Hive, RagnarLocker, ALPHV, LockBit, 8Base) across ~5.5 six-month windows ≈ 27.5 group-windows; 5 disruptive events → ~18%/group/6 months. Primary sources cited below.
- Adjustment ledger (log-odds): +0.20 LE momentum (Cronos/Phobos/8Base), +0.08 target priority from Cl0p’s large-scale exfil/extortion model (e.g., MOVEit per CISA), -0.10 infiltration difficulty (low affiliate surface), -0.05 sanctuary/jurisdictional limits → net +0.13 → 20%.
- Sensitivity: 16–24% given uncertainty in exposure denominator and future LE tempo.
AlphaHunt Converge - Plug in your Flight Crew
Get intelligence where it counts. No dashboards. No detours. AlphaHunt Converge teases out your intent, reviews the results and delivers actionable intel right inside Slack. We turn noise into signal and analysts into force multipliers.
Anticipate, Don’t Chase.
Top Drivers
- Law-enforcement tempo and capability: recent multi-country operations (ALPHV disruption 2023; LockBit disruption/charging and extraditions 2024–2025; 8Base arrests and server takedowns 2025).
- Cl0p’s operating model: since 2021, shift toward data-theft mass exploitation campaigns (e.g., MOVEit) raises political priority and investigative pressure.
- Jurisdictional constraints: probable operation from non-cooperating or hard-to-reach jurisdictions lowers odds of arrests/servers seized in-country.
- Infiltration surface: Cl0p’s more centralized, episodic model (not a broad RaaS) reduces affiliate-based infiltration avenues.
- Resilience/mirroring: extortion sites often reappear quickly on new onion services unless LE achieves server-level control.



![[DEEP RESEARCH] Who’s Most Likely to Abuse MCP Integrations? UNC3944, TraderTraitor, UNC6293](/content/images/size/w600/2026/03/z.png)

![[FORECAST UPDATED] AI Agents as Regulated C2: Will Anyone Be Forced to Act?](/content/images/size/w600/2026/02/z-11.png)
![[FORECAST] Fortune 500s: Will Prompt Injection Trick IDE Agent Mode into Running Commands—or Leaking Secrets—by 2026?](/content/images/size/w600/2026/02/z-10.png)